IT FOR THE ANYWHERE BUSINESS
IT Services for local businesses.
Look to CMIT Solutions for local, friendly IT specialists who are always close by and ready to take your business anywhere you want to go.
Explore Options
Your network of support.
We provide a local presence plus the resources of a large system with more than 250 locations in North America and partnerships with leading technology providers.
Have you seen our reviews?
Check Out Client Reviews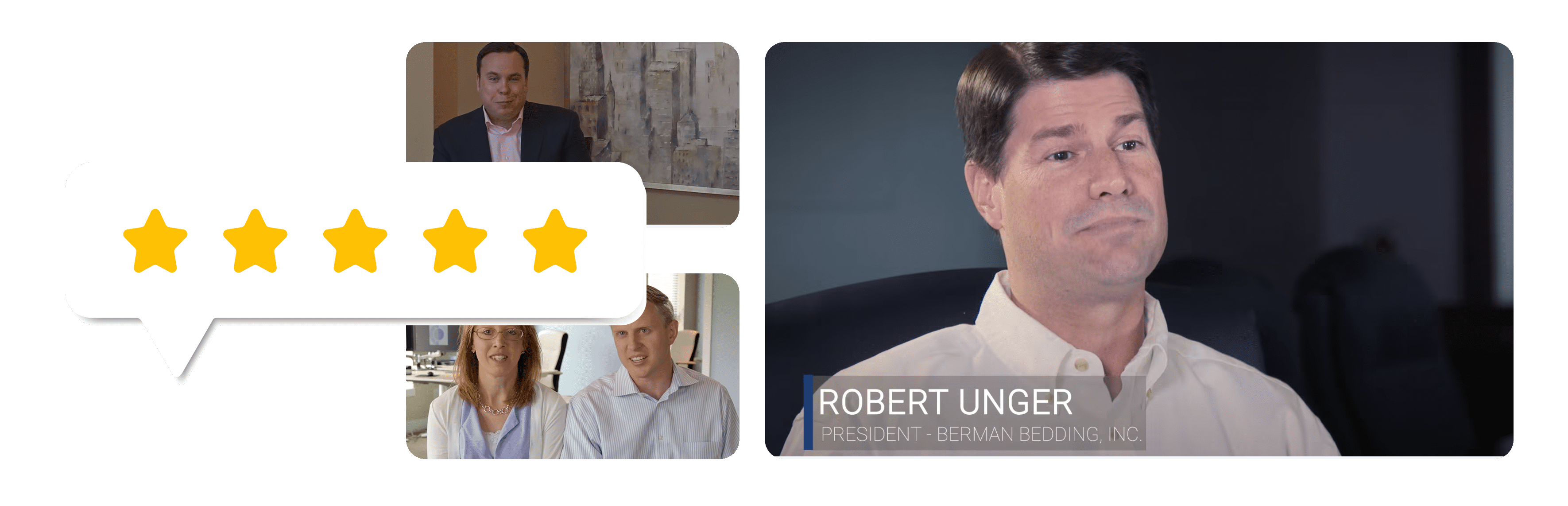
NEXT STEPS
Contact us for a quick consultation.
"*" indicates required fields
Learn how 24/7 proactive IT and cybersecurity monitoring can help your business succeed.
Let’s Talk
WHY CMIT
What makes CMIT unique?
With CMIT Solutions, you don’t have to choose between advanced technology and personalized attention.
We combine the best in technology with individualized services.
CMIT Solutions serving Virginia Beach
Although every company is different, the one thing that all businesses have in common is a dependence on technology. Everyone needs working tech to some extent, and computer or internet crashes can cause costly delays.
Instead of wasting time and energy trying to fix the IT issues, call CMIT Solutions serving Virginia Beach, Chesapeake, Norfolk, Suffolk, Hampton, and the surrounding areas.
How We Help Businesses in Virginia Beach
Some IT issues can be solved with a simple bug fix, and our local, friendly experts are ready to help! However, if you need more extensive services, we can set up repeated visits, a unique customer relationship, and a plan to expand your technology and grow your company.
Personalized Technology Solutions
No matter how large or small your company is, IT help is crucial to get to the next step of growth. Whether you need new cybersecurity options, more cloud storage, or a network upgrade, CMIT Solutions serving Virginia Beach can help you find the perfect, unique solution.
Take IT off your to-do list.
Technology should support your business, not the other way around. We offer a full suite of solutions to handle the growing complexity of IT and cybersecurity so you can stay focused on growing your business.












