FAQs
What is included in your managed cybersecurity solutions?
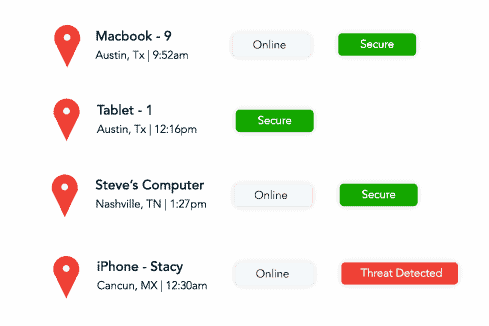
Our managed cybersecurity solutions include 24/7 threat monitoring, multi-layered protection, compliance management, endpoint security, and risk assessments. We customize these services to fit your business needs, ensuring your sensitive data remains secure and compliant with industry regulations.
Who needs cybersecurity services?
Any business handling sensitive data, financial records, or customer information needs cybersecurity services. Whether you’re a small business or a large enterprise, proactive measures are essential to prevent cyberattacks and maintain operational security.
What makes CMIT Solutions’ cybersecurity services unique?
We offer tailored, multi-layered cybersecurity strategies backed by 24/7 monitoring, advanced tools like SIEM and SOC, and expert guidance. Our solutions go beyond basic defense, focusing on compliance, continuous protection, and adapting to your specific business challenges.