The cost of a data breach can be enormous, leading to not only financial losses but also damage to a company’s reputation, customer trust, and the potential for legal repercussions. Penetration testing can be seen as a form of preventative maintenance for your cybersecurity infrastructure. 70% of companies do penetration tests for vulnerability management program support, 69% for assessing security posture, and 67% for achieving compliance according to CoreSecurity’s Penetration Testing Report.
By investing in regular testing, you’re essentially making a much smaller investment in security than you would in the event of a breach. This blog post delves into the critical role of penetration testing and underscores its indispensability as a cornerstone of any effective cybersecurity strategy.
WHAT IS PENETRATION TESTING?
Penetration Testing, or pen testing, is a simulated cyber-attack on a computer system, performed to evaluate the security of the system. The test is designed to identify vulnerabilities and to provide an organization with a realistic assessment of their security posture. It can involve the attempted breaching of application systems, network systems, and other types of secure systems to find potential points of vulnerability.
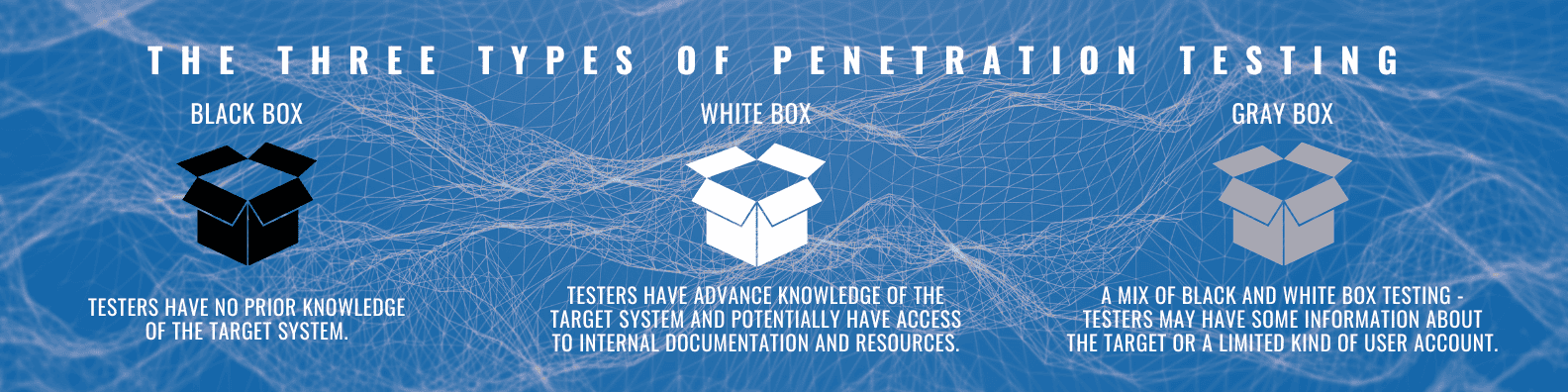
There are mainly three types of penetration testing:
Black Box Testing: Testers have no prior knowledge of the target system.
White Box Testing: Testers have advance knowledge of the target system and potentially even have access to internal documentation and resources.
Grey Box Testing: A mix of Black and White Box testing, in which testers may have some information about the target or a limited kind of user account.
HOW IS IT DONE?
A skilled pen tester will begin by gathering information about the target before using that information to test various entry points. The process can be broken down into multiple phases, including reconnaissance, scanning, gaining access, and maintaining access. The main goal is not just to identify weaknesses but to test the reaction of the organization’s security team to the intrusion attempt.
WHO NEEDS PENETRATION TESTING?
The Small and Mid-sized Enterprise Dilemma
Many small and mid-sized enterprises (SMEs) often assume they are not at risk and may not have a strategic cybersecurity plan in place. However, due to the increasing trend of cybercriminals targeting easy-to-breach systems, SMEs should see pen testing as a vital part of their business continuity planning.
Corporate Security Teams
For larger businesses, a strong security team is the backbone of cybersecurity efforts. Penetration testing offers these teams a way to objectively evaluate their defenses and to fine-tune their incident response plans.
Individuals in IT and Security Roles
Professionals in IT roles, especially those in security, must spearhead the initiative to introduce penetration testing within their organizations. This proactive approach can save the business from potentially catastrophic security incidents.
THE BENEFITS OF PENETRATION TESTING?
Identify Security Weaknesses
The most obvious benefit of pen testing is that it uncovers specific weaknesses within your IT infrastructure, allowing you to address them before an attacker does.
Compliance with Regulations
Many industries are subject to stringent security regulations. Regular penetration testing can ensure that businesses remain compliant with industry standards and regulations.
Business Continuity and Disaster Recovery
By identifying and addressing vulnerabilities, penetration testing helps businesses fortify their disaster recovery strategies and ensures that their essential business operations can continue in the event of a security breach.
THINGS TO CONSIDER BEFORE IMPLEMENTING
Internal vs External Testing
Deciding whether to conduct penetration testing with in-house resources or to outsource to a specialist depends on many factors, including the complexity of the network and the skill level of available personnel.
Frequency of Testing
The frequency of testing should be determined by the rate of change within your network. Organizations undergoing frequent changes, such as software updates or infrastructure modifications, may need more regular testing.
Reporting and Analysis
The value of pen testing lies in the detailed reports that provide actionable insights. It’s essential to have a clear reporting and analysis process in place to take full advantage of the test results.
THE TAKEAWAY
Penetration testing is not a one-time action but an ongoing process. It provides invaluable insights into the vulnerabilities present in your system and helps you to reinforce your cybersecurity strategies constantly. Whether you’re a small business owner or a corporate CIO, understanding the necessity of penetration testing is the first step in safeguarding your digital assets against the growing tide of cyber-attacks.
Penetration testing is gaining so much traction that it is estimated that by 2025, it will be a $4.5 billion industry (Gartner). If you’re asking whether your business really needs penetration testing, the answer is a resounding yes. It’s not just about meeting industry standards or satisfying compliance requirements; it’s about securing your business, your customers, and your future. Make penetration testing an integral part of your cybersecurity initiative — the investment now will pay dividends in the long run.
Written by: Chris Zambuto | Chief Information Security Officer @CMITBostonCambridge