Top Cybersecurity Recommendations for Healthcare
The healthcare industry is increasingly relying upon internet-connected devices and solutions to improve patient care, organizational efficiency, speed of crisis response, and much more. The emergence of telemedicine, digital health records, internet-connected medical devices, patient wellness apps, and an increasing amount of third parties entering the health supply chain has created many benefits, but has also exposed the industry to vulnerabilities that cyber criminals regularly attempt to exploit.
The third week of Cybersecurity Awareness Month delves into the industry (hospitals, care facilities) and consumer (telemedicine patients) implications of internet-connected device use, and what steps both can take do their part and #BeCyberSmart.
For Telemedicine Patients / Consumers
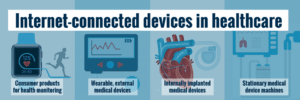
There are seemingly countless medical devices and apps documenting everything from the number of steps people walk to monitoring sleep cycles and heart rates. These internet-connected medical devices generally fall into four categories: consumer products for health monitoring (fitness trackers), wearable external medical devices (insulin pumps), internally implanted medical devices (pacemakers), and stationary medical devices (hospital or hospice-based monitoring machines).
Due to the pandemic, many more patients and clinicians have relied heavily on telemedicine. Patients need to understand they have rights while using these devices and when sharing information recorded. [vc_custom_heading text=”Talk to your provider about their security and privacy practices:” font_container=”tag:h1|font_size:20|text_align:left|color:%23ef4136″ use_theme_fonts=”yes”][vc_column_text] While you can’t control your provider, you can do your best to protect your health information.
- Ask your healthcare provider about their security and privacy practices.
- Make sure your devices are updated if you are going to use them for telemedicine.
- Carefully review your health information while online using a secured connection and only save or download health information to a safe location.
- If your provider had a data breach, review what information was compromised and follow our guidelines for limiting the impact of the breach.
- Ask to purchase healthcare devices and apps with proven safety. Many devices come preloaded with default passwords and lack encryption and software updates. Be a well-educated consumer and do your research.
- Implanted medical devices are another overlooked security challenge that is only going to increase over time.
For Healthcare Organizations
It’s about time the healthcare industry starts thinking more like technology companies regarding cybersecurity. Virtually every week we hear of a new data breach or compromise in healthcare. Recently, Universal Health Services experienced a massive ransomware attack that crippled their network and computer systems. These breaches can sometimes affect thousands, hundreds of thousands and even millions of patient records.
Here’s the top cybersecurity recommendations healthcare providers should be doing to safeguard their organizations:
1. Cybersecurity Awareness Training
Cybersecurity Awareness Training for staff & patients helps stop potential breaches inside and outside the organization.
2. Vulnerability Scan Assessments
Perform Vulnerability Scanning to prioritize mitigation efforts towards the most at-risk systems and devices first. The CISA and FBI identified the top 10 routinely exploited cyber vulnerabilities and is a good starting point for security teams with scarce resources.
3. Security Incident Simulation Testing
Security Incident Simulation Testing evaluates the cybersecurity health of medical systems, devices and staff awareness. Test, re-train and be aware of potential vulnerabilities.
4. Data Recovery Backup Systems
Install Data Recovery Backup Systems to mitigate the damage from a breach or security incident. Having a good recovery process in place saves both time and money. It is also important to test those backups regularly.
5. Authorized Access Management
Implement Authorized Access Management to prevent and alert unauthorized data access. Paired with MFA, this privileged access can prevent the spread of malware across systems due to limiting data access points.
6. Prioritize IoT Devices with Proven Security
Prioritize IoT Devices with proven security. Not all medical devices are created equal. Security teams should weigh in suggesting devices that utilize a baseline of security capabilities.
Do Your Part. #BeCyberSmart
Take the time to read through our previous blogs to get the facts about cybersecurity. Staying safe online requires knowing what the risks are and how to best defend yourself and your organization from these risks. Understanding how the hackers think and act, is a starting point for defending yourself from them and ensuring the security and privacy of your data and your company’s data.
Stay tuned each week in October as we’ll cover a new topic for Cybersecurity Awareness Month.
Written by: Chris Zambuto | Chief Information Security Officer @CMITBostonCambridge