All hardware and software is subject to the march of time, and CMIT works to monitor the age and potential degradation of all your devices ahead of time so clients can be aware of what needs to be replaced and when, as well as what those replacements may cost. In this blog post, our Senior Technical Manager & Project Management Lead, Zach Jones, covers what makes up a tech refresh strategy and why every company needs this in their overall IT strategy.
Q: WHAT IS A TECH REFRESH?
ZJ: A tech refresh, in simple terms, is the process of replacing hardware and software on a regularly scheduled basis based on hardware age and software needs. Some hardware may simply become obsolete and no longer meet the needs of a business, other hardware/software may not be compatible with new versions of operating systems or applications, and general hardware degradation over time may all play a factor into the timing and recommendation of a tech refresh.
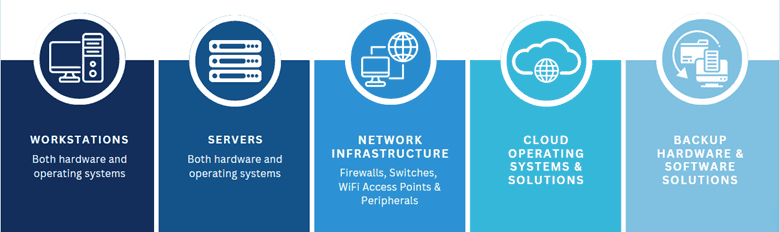
CMIT evaluates all IT infrastructure hardware and software as part of the tech refresh process, including the following:
Q: WHEN IS THE TECH REFRESH TIMEFRAME?
ZJ: CMIT typically recommends a 5-year refresh period for desktop and laptop computers, a 5-year refresh period for networking devices, and a 6–7-year refresh period for physical servers. Software follows timelines dictated by software vendors, and typically dictates around a 5–8-year period before going end of life. There may be exceptions to that methodology, but that is the general idea. These recommended refresh periods are in place for several reasons:
- Based on our experience, physical hardware begins breaking down over time, and the likelihood of a catastrophic failure like a hard disk failing begin steadily increasing as devices near those recommended refresh periods.
- Manufacturers will often not allow purchase of renewed warranties for hardware of a certain age, hence the lifecycles we recommend.
- Though CMIT recommends purchasing hardware best suited to your environment, new hardware is constantly being developed, and older hardware will not perform as well with the latest operating systems and software, leading to loss of productivity from older, slower hardware.
- CMIT also monitors software end-of-life dates, and advises upgrades ahead of time to ensure proper patching/security and no loss of function.
Sample Technology Assessment:
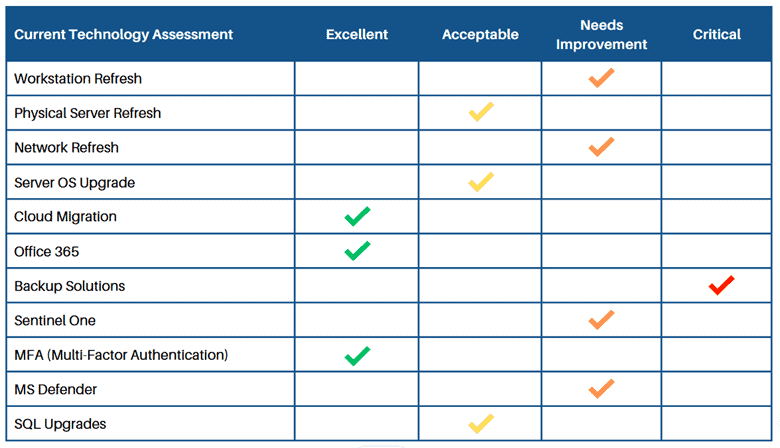
ZJ: CMIT is responsible for the care and maintenance of all client hardware under our management. All managed hardware, from workstations and servers to firewalls and switches, and everything in between are subject to careful scrutiny for day-to-day infrastructure maintenance, but CMIT also focuses on the big picture to plan for a healthy, stable fleet of devices.
CMIT is partnered with many reputable, business grade hardware and software vendors and as such can help purchase at very competitive pricing. We can handle the process from top to bottom — procurement through deployment. We also document and manage the devices, so monitoring for issues, replacing via warranty, etc., are all functions of the “after” process of the tech refresh.
YOUR TECHNOLOGY ROADMAP
Ultimately the goal of a tech refresh is to ensure that your organization can function at the highest level of productivity with minimal chance of hardware failure and loss of ability to conduct business. The tech refresh process helps to plan for what infrastructure will inevitably need to be replaced and allow you to plan on a budgetary level well ahead of time. Think of the tech refresh process as a roadmap for your technology, with CMIT laying out any potential roadblocks ahead of time to avoid any unnecessary hardship along the way.
Written by: Zach Jones | @CMITBostonCambridge
About Zach Jones
Zach manages multiple hats including a senior resource for remote technical issues and implementation projects. He is a key resource for new equipment acquisitions.