Vulnerability management is a fundamental aspect of an information security and privacy program. If done well it provides a strong foundation for your company, its data and your clients’ data. Done poorly, and the doors are wide open for your company to be hacked, its data breached, and your clients’ privacy violated. Only 14 percent of small businesses rated their ability to mitigate cyber risk and vulnerabilities as useful. So, you know it’s important, but what is vulnerability management and how is it achieved?
At its core, vulnerability management involves:
IDENTIFYING THE DEVICES IN YOUR ORGANIZATION
This can include servers, workstations, IoT devices, routers, switches, firewalls, mobile phones—basically anything connecting to your network.
ASSESSING SECURITY WITH A VULNERABILITY SCAN
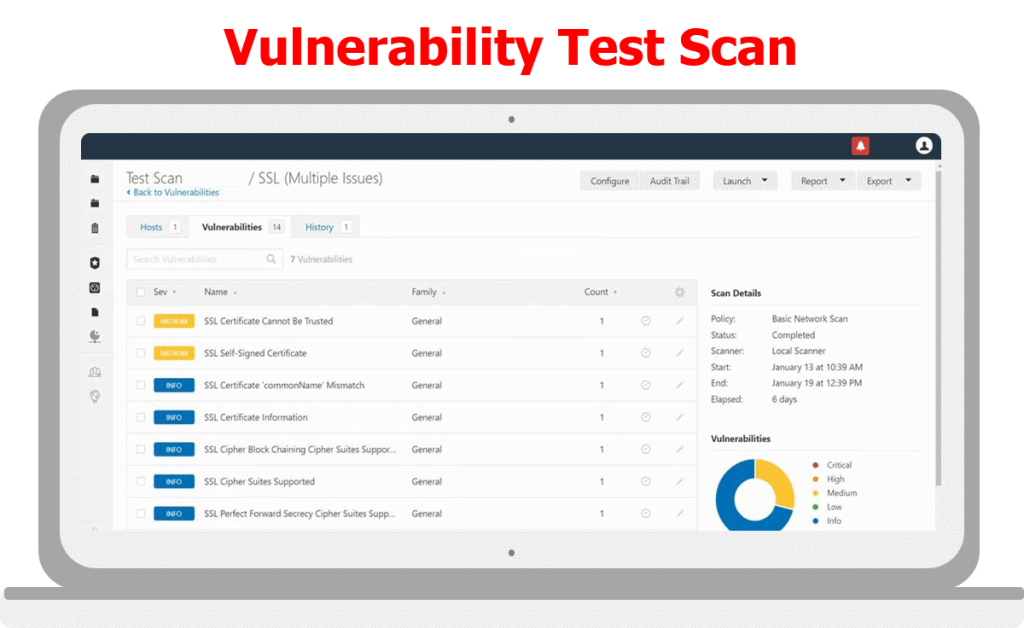
Next, you need to assess all of those devices. Typically, this is done via a vulnerability scan. A vulnerability scan involves scanning each device to determine what they are, any vulnerabilities or weaknesses that exist in those devices and providing a report about those vulnerabilities.
REMEDIATING AND MITIGATING VULNERABILITIES
Remediation and mitigation are a critical aspect of the vulnerability management process. During this phase of the process vulnerabilities identified during the vulnerability scan are reviewed in detail to understand how to best address them. In many cases the vulnerabilities can be remediated by applying patches, updating the operating system or firmware, or updating an application. Sometimes, extensive changes must be undertaken to address vulnerabilities such as disabling older insecure protocols, rearchitecting a system or switching to a more secure service or application.
Oftentimes it is not possible to completely remediate a vulnerability. This is a frequent occurrence for legacy systems or apps. These older platforms continue to be used for a critical business function but cannot be updated for any number of reasons. When this happens, other mitigations can be put in place such as creating a “sandbox” for a system that cannot be updated or otherwise made not vulnerable. A sandbox is a protected network that has limited access to or from it in order to limit the exposure of a vulnerable system. Sandboxing effectively disables some services by reducing the number of vulnerabilities associated with a system. If that is not possible, documenting that a given system must remain in a vulnerable state is critical because it is needed for a business purpose and cannot be updated or migrated.
SAFEGUARD YOUR ORGANIZATION
A robust vulnerability management program becomes the cornerstone of a company’s information security and privacy posture. Vulnerability management helps prevent hacking and data breaches, while protecting the privacy of your data and your company from legal liability. It effectively acts a shield to safeguard your organization. Neglecting vulnerabilities will only leave your organization susceptible to a data breach – and SMBs are known to underestimate the cost. Your trusted CMIT advisor performs vulnerability scans and remediation. Please contact us for more information. We’re always here to help.
Written by: Chris Zambuto | Chief Information Security Officer @CMITBostonCambridge