Ready To Test Your Cybersecurity Awareness?
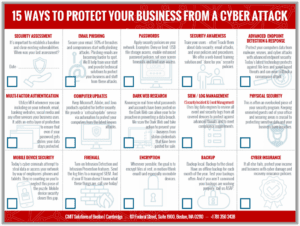
October is Cybersecurity Awareness Month. Did you know… one in five small businesses will suffer a cyber breach this year? 81% of all breaches happen to small and medium sized businesses? And that 97% of breaches could have been prevented with today’s technology? To help boost awareness, we compiled a Cybersecurity Awareness Checklist with the 15 most effective tactics your security team should be doing to protect your company, your staff, and your clients’ data from a cyber-attack.
DOWNLOAD the 15-Point Cybersecurity Awareness Checklist HERE
The 15 Most Effective Cybersecurity Tactics To Protect Your Business
Want to know where your company stands? Check out the Cybersecurity Awareness Checklist and read on to see how well your organization is protected.
1. Security Assessment
A security assessment seeks to identify both the good security and privacy practices an organization has in place, identify gaps and then document the steps needed to close them. It’s important to establish a baseline and roadmap for your cybersecurity and privacy program. A security assessment provides that framework and enables a company to develop a comprehensive plan to address deficiencies. We’ve found that 90% of IT employees lack confidence in their companies’ ability to detect IT problems. When was your last assessment?
2. Phishing Emails
Secure your email. Roughly 90% of breaches and compromises start with phishing attacks. Phishing emails are becoming harder and harder to spot. Even when detected, nearly half of organizations reported that it takes a day or longer to remove phishing emails from endpoints once a phishing attack is reported to the security team—largely due to a lack of manpower. We’ll help you train your staff and provide technical solutions to protect your business and staff from these attacks.
3. Passwords
A password policy that provides for strong password and passphrases, requires users to use different passwords for different accounts and leverages password safes is another key piece to a robust cybersecurity program. Weak password policies make hackers’ jobs easy. Knowing these four key steps can help secure your passwords. What’s your password policy?
4. Security Awareness
Train your users – often! Teach them about data security, phishing attacks, and your policies and procedures. We offer a variety of training solution which can be tailored to your business and its needs. Security-related risks are reduced by 70% when businesses invest in cybersecurity awareness and training.
5. Advanced Endpoint Detection & Response (EDR)
Protect your computers data from malware, viruses, and cyber-attacks with advanced endpoint security. Today’s latest technology protects against file-less and script-based threats and can even rollback a ransomware attack.
6. Multi-Factor Authentication (MFA)
A staggering 81% of hacking-related breaches leverage either stolen and/or weak passwords. It is crucial to utilize MFA whenever you can—including on your network, email, banking websites, social media and any other services your business uses. MFA adds an additional layer of protection to ensure that even if your password gets stolen, your data still stays protected.
7. Computer Updates
Keep your operating system, iOS and third-party software up to date (e.g., Adobe, Chrome and Java products). According to the 2018 Trustwave Global Security Report, 100% of web applications tested displayed at least one vulnerability, with 11 as the median number detected per application. We provide vetted, automated updates for your workstations, servers and third-party patching. Are your machines and devices up to date?
8. Dark Web Research
Knowing in real-time what passwords and accounts have been posted on the Dark Web can allow you to be proactive in preventing those credentials from being used by hackers to access your personal or sensitive information. We scan the Dark Web and take action to prevent your business from stolen credentials that have been posted for sale.
9. SIEM / Log Management (Security Incident & Event Management)
Uses big data engines to review all event and security logs from all covered devices to protect against advanced threats and to meet compliance requirements. Intel Security reports that 93% of security personnel are overwhelmed by alert data and unable to triage all potential threats.
10. Physical Security
Physical security is an often overlooked piece of your security program. Make sure your main entrances and exits are protected. Also, protect areas with sensitive documents and computer equipment by limiting access to authorized individuals. Keeping uninvited guests out of your office and securing areas is crucial to protecting sensitive data and your business from breaches.
11. Mobile Device Security
As many as 91% of businesses plan to have a mobile workstyle strategy in place, while 62% already have one according to insight.com. Cyber criminals attempt to steal data or access your network by way of employees’ phones and tablets. They’re counting on you to neglect this piece of the puzzle. Mobile device security closes this gap.
12. Firewall
Firewalls are a critical piece of your security infrastructure. Improperly configured, they can allow hackers into your internal network allowing them to bypass your filters. Properly configured firewalls, leveraging the latest tools, provide a baseline of protection for your company.
13. Encryption
A laptop is stolen every 53 seconds. Whenever possible, the goal is to encrypt files at rest, in motion (think email) and especially on mobile devices. Encryption of sensitive data can help limit the impact of stolen devices and provides a safe harbor in some regulations.
14. Backups
Backups are critical as they protect your company from accidental or intentional data loss. They also protect your data from Ransomware. Having up to date backups adds an additional layer to your security program. Backup local. Backup to the cloud. Have an offline backup for your company’s data. Test your backups often. And if you aren’t convinced your backups are working properly, call us ASAP.
15. Cyber Insurance
If all else fails, protect your income and business with cyber damage and recovery insurance policies. Cyber insurance policies can be complex and overwhelming. Make sure you work with a professional insurance agent and that you fully understand the coverage limits of your policy.
How Secure Is Your Company?
Hopefully your run through the checklist went well. Maybe it opened your eyes to a few cyber security blind spots in your organization and inspired you to take action to secure your business. Still unsure where to start? A great first step is to perform a security assessment. This will help identify the areas for improvement and enable your company to develop a roadmap with recommendations tailored to your environment. Remember that the hackers don’t rest, so act now to begin addressing your company’s cybersecurity program. Contact your trusted CMIT advisor if you need help.
Written by: Chris Zambuto | Chief Information Security Officer @CMITBostonCambridge