In today’s diverse business landscape, generic IT solutions frequently fall short for organizations handling sensitive data. Why? Supporting operational needs while meeting rigorous compliance frameworks like GDPR and HIPAA presents a critical challenge for businesses.
Off-the-shelf systems often lack the precision to address unique workflows and security demands—a gap that exposes businesses to breaches and compliance violations. That’s why working with an IT solution company that understands compliance nuances becomes critical.
Customized IT solutions and compliance services from trusted IT service providers like CMIT Solutions offer:
- Adapting tools to mirror organizational workflows.
- Pre-engineering compliance requirements into IT architecture.
- 24/7 monitoring for regulatory alignment.
This strategic approach turns technology from a compliance hurdle into a trust-building asset.
This article will delve deeper into why tailored IT and compliance strategies are essential for today’s businesses, exploring practical approaches and the benefits of partnering with the right experts.
Who Are One-Size-Fits-All IT Solutions Good for?
There are numerous one-size-fits-all IT solutions available. While custom IT solutions get a lot of attention, standardized offerings can be the perfect choice for many businesses. These solutions come from both industry giants and specialized boutique providers. Though some organizations hastily choose these options to simply complete their IT initiatives, it’s worth considering who truly benefits from this approach.
A one-size-fits-all solution might be ideal for your business if:
- You need minimal customization – You’ve thoroughly evaluated the product’s features and capabilities and are confident it will fulfill your requirements without modifications.
- You require quick implementation – These solutions typically deploy faster than custom alternatives, allowing your team to adopt and benefit from new systems more rapidly.
- You have budget constraints – With their predictable pricing structure, these solutions work well for organizations with fixed budgets that don’t anticipate needing significant customizations or workarounds later.
However, these solutions also have downsides by often overlooking your unique business needs and critical workflows, frequently falling short. Furthermore, forcing processes into rigid systems hurts operational efficiency and creates security gaps. You might pay for unneeded features while lacking vital safeguards.
Rigid IT solutions hinder SMBs. Why? They may not be the right option as they:
- Lack the scalability for growth, as your organization requires technology that can precisely adapt as your business grows.
- Use generic security features that may not adequately protect your most sensitive information or address specific risks.
- Force standardized workflows when your business requires tailored functionality unique to your operations.
This gap is apparent. Understanding these limits is the first step toward evaluating options, like customized IT solutions and compliance for business, that truly match your workflows and prepare you for better solutions.
Why a Customized IT Solution is Best for Your Business?
Customized IT solutions and compliance for businesses deliver tangible value because they:
- Fit into your workflows, creating natural pathways for operational efficiency to flourish.
- Eliminate unnecessary system clutter, creating clearer digital workspaces, directly boosting productivity.
- Reduce wasted license costs with features selected for your exact operational needs.
- Prevent compliance oversights through security controls mapped to your unique risk environment.
- Enable seamless scalability as your client base expands without costly system replacements.
Furthermore, enhanced security emerges organically through this approach. For example, specific encryption protocols can protect sensitive data flow at precise transaction points rather than merely blanketing your entire network infrastructure. Certified MSPs (Managed Service Providers) configure these precise safeguards while maintaining accessibility for authorized personnel across all departments.
Finally, this synergy of optimized workflows and targeted security positions organizations to achieve more with less complexity. By transforming technology from a restrictive framework into an adaptable and flexible productivity partner, you create the infrastructure needed to support, not hinder, your strategic business goals, setting a solid foundation for rigorous compliance management.
The Importance of Compliance for Businesses
There are high-risk operational realities where customized IT solutions prove essential, particularly for businesses in highly regulated industries handling sensitive data.
GDPR-governed organizations face strict data privacy mandates. Hence, they need systems designed for rigorous information safeguarding. Financial institutions and healthcare networks demonstrate how tailored technology delivers results.
Financial businesses require risk-aware infrastructure meeting SOX controls and Basel III requirements. Healthcare providers need HIPAA-aligned systems ensuring protected access to medical records. Let us examine why this precision matters:
Key regulatory drivers include:
Financial
The GLBA Safeguards Rule requires financial institutions to protect customer information through appropriate safeguards based on risk assessment. Additionally, PCI DSS compliance mandates specific encryption standards for payment card data, requiring organizations to encrypt cardholder data during transmission over open networks and implement strong access controls for stored payment information.
Healthcare
HITECH Act compliance strengthens HIPAA enforcement and promotes EHR adoption with requirements for auditing and access controls (implicit logging), but it doesn’t universally mandate real-time access logging. The HIPAA Security Rule requires mechanisms to log and review access, but the specifics (including real-time) depend on risk analysis.
Global Standards
GDPR requires companies to use appropriate technical and organizational measures to secure data. It suggests using methods like encryption and pseudonymization, but it doesn’t explicitly require end-to-end encryption for all situations.
The choice of measures depends on risk assessment. Audit trails (logs) are generally essential for accountability and security monitoring. While they are necessary as technical/organizational measures, they are not specifically mentioned as “audit trails” in the main articles.
Generic tools can’t embed industry-specific controls needed for these scenarios, often leaving organizations vulnerable. In contrast, those partnering with expert IT solution providers avoid reactive compliance traps—they pre-adapt systems through continuous vulnerability mapping.
This strategic alignment keeps managed businesses audit-ready through:
- Precise encryption
- Access controls
- Automated compliance reports
Also Read: Understanding Professional IT Services’ Role in Real Estate
How IT Service Providers Help Businesses Remain Compliant
Why struggle with compliance demands and complex IT security alone when you can leverage strategic partners? MSPs often act as your specialized co-pilots, blending deep technical expertise with valuable industry-specific insights. Consequently, they align your IT infrastructure directly with evolving regulatory requirements, moving beyond simple fixes. However, remember that compliance is a shared effort.
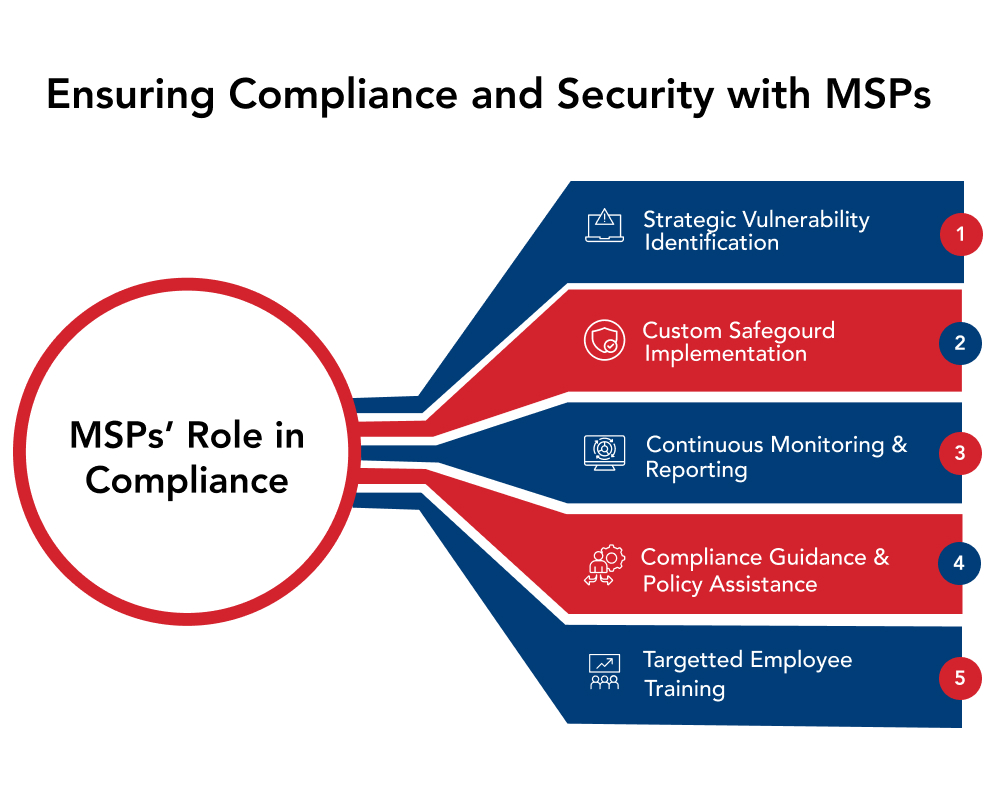
Here’s how expert MSPs deliver customized support:
- Strategic Vulnerability Identification: They uncover security weaknesses and potential compliance gaps through comprehensive risk assessments tailored to your sector’s regulations.
- Custom Safeguard Implementation: Furthermore, MSPs can deploy robust security controls, such as precise data management protocols, strong encryption methods, and user access controls designed to mirror standards like HIPAA or GDPR.
- Continuous Monitoring & Reporting: They maintain constant vigilance over your systems, providing automated monitoring and detailed reports to ensure ongoing alignment and quick incident response.
- Compliance Guidance & Policy Assistance: Skilled MSPs help develop and refine internal policies, ensuring they meet necessary standards and support your staff’s understanding.
- Targeted Employee Training: Many offer specialized training programs, including security awareness and phishing simulations, to equip your team with best practices for protecting information.
Are you ready to transition from reactive IT fixes to a proactive, compliance-first strategy? MSPs can help transform these burdens through customized IT solutions and compliance for businesses.
Addressing Unique IT Compliance Challenges Faced by SMBs
Small businesses face a unique paradox in the digital age. While technology remains essential for mission-driven operations, most IT solutions fail to adequately address both evolving security risks and precise compliance demands.
Two critical limitations expose SMBs using generic IT:
- Compliance Misfits: Systems often can’t align with specific compliance regulations like HIPAA for client data or unique audit protocols.
- Blind Security Spots: Fixed protections ignore vulnerabilities unique to industry-specific specialization, risking data security.
Why does this matter intensely? Mission-driven work relies on sensitive financials, client records, and personal identities, where data breaches could collapse public trust overnight.
Therefore, selecting the right MSP partner is crucial. Consider asking potential partners key questions:
- How will your solutions help us meet specific reporting requirements?
- Can your services scale efficiently during peak periods, such as disaster relief drives or year-end campaigns?
- What predictable pricing models do you offer that align with the budget cycles and organizational size?
Secure Your Operations With Tailored IT & Expert Guidance
In the digital age, navigating compliance and ensuring operational efficiency is an ever-changing challenge. Generic IT systems may work for basic needs, but they leave growing businesses exposed, especially when handling sensitive data. In contrast, customized IT solutions bridge operational efficiency with ironclad compliance.
One-size-fits-all only works for scarves and playing cards. Compliance isn’t optional for businesses, particularly SMBs; it’s mission-critical.
At CMIT Solutions, Princeton, we deploy compliance-first technology roadmaps, helping businesses in the Highland area meet rigorous standards while redirecting savings toward community impact. Let us handle the technology complexities while you focus on strategic goals.
Ready to transform IT burdens into strategic assets with customized IT approaches and compliance services? Connect with our team today to customize your IT workflows and ensure compliance!