FAQs on Cyber Protection Solutions
Who Needs Cybersecurity Support?
Any organization that uses digital systems to access, store, or manage sensitive information needs cybersecurity support. Regardless of size or industry, every business is vulnerable to cyber threats and must take proactive steps to protect its data and systems.
This includes implementing secure authentication methods, using encrypted cloud storage, and maintaining intrusion detection systems. Businesses also benefit from regular software updates, risk assessments, and best practices like encryption protocols and limiting unnecessary user access.
As threats continue to evolve. from malware to ransomware, ongoing education, strong technical defenses, and a strategic cybersecurity plan are essential for preventing data loss, avoiding costly disruptions, and staying compliant with industry regulations.
What Does Cybersecurity Support Include?
CMIT Solutions offers comprehensive cybersecurity services that go far beyond virus prevention. Our support includes tailored software designed to secure sensitive data and prevent unauthorized access, along with solutions that help assess current vulnerabilities and reduce risk.
We also prioritize regulatory compliance to ensure your systems meet industry-specific requirements. Our experienced team provides around-the-clock protection, including user management, firewall implementation, and endpoint monitoring.
Because no two businesses face the same threats, our solutions are customized to deliver the highest level of protection, giving you confidence in your cybersecurity posture.
What Are the Most Important Components of a Cybersecurity Package?
A complete cybersecurity package must address compliance, risk management, system monitoring, and user behavior. Compliance ensures your business meets legal and industry regulations through secure data handling practices. Software solutions play a critical role by detecting threats, filtering harmful content, and tracking network activity.
Cyber threat awareness is equally important, your staff must be trained to identify and respond to potential risks like phishing attempts or weak passwords. Risk mitigation involves creating plans for incident response and data recovery to reduce the impact of attacks.
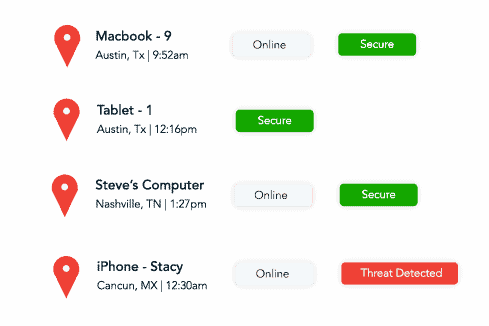
Finally, continuous monitoring through technologies like SIEM and oversight from a Security Operations Center helps detect suspicious activity and respond in real time. Together, these components form the foundation of a resilient cybersecurity strategy.
Data Compliance
Data compliance ensures that your business adheres to all relevant laws and industry regulations. This involves more than just legal formality, it requires practical security measures such as antivirus implementation, secure data handling procedures, and maintaining routine data backups to protect sensitive information and ensure business continuity.
Software Products
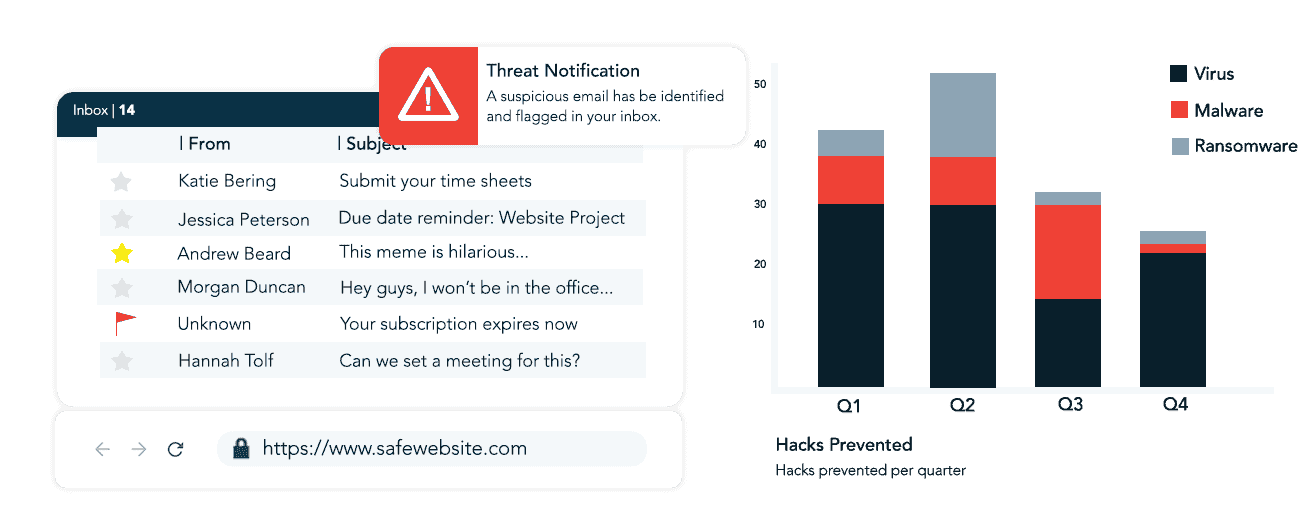
Effective cybersecurity relies heavily on the right software. Tailored security programs help detect, block, and respond to threats in real time. These tools may restrict access to risky websites, monitor internal network activity, or flag and quarantine suspicious email messages before they reach end users.
Cyber Threat Awareness
Your employees are your first line of defense. That’s why it’s essential they understand the risks they may face, especially phishing attempts and social engineering tactics. Ongoing training, awareness campaigns, and enforced policies such as strong password requirements all contribute to a more secure workplace.
Mitigate Potential Risk
An effective cybersecurity strategy must be prepared to address any potential risk before it escalates into a major incident. This includes developing comprehensive incident response plans, establishing data loss prevention policies, and conducting regular penetration testing. These proactive steps help identify vulnerabilities early and ensure your business can respond swiftly and effectively in the event of a cyberattack.
Monitor Cyber Activities
Continuous monitoring is key to catching threats before they cause damage. Leveraging tools such as Security Information and Event Management (SIEM) and services from a Security Operations Center (SOC) allows for comprehensive visibility. These systems log, analyze, and respond to suspicious activity across your network in real time, helping to prevent breaches and ensure fast containment.