6 Types of Hackers: From Black Hat to Red Hat—Know Your Enemy!
November 26, 2023
Do you ever wonder who is behind all those cyberattacks that steal private information or cause mayhem online? Well, there are many different types of hackers out there, from black hats to red hats and everything in between. We’ll explore the six distinct categories of hackers – from the nefarious to the noble – so you will know exactly all the hats and who’s behind each attack along with their objectives. Whether you’re looking for practical advice on how to stay safe from cyber threats or just curious about who is behind some of these high-profile hacks, read on to discover more about hacking culture and terminology.
Who are these hackers?
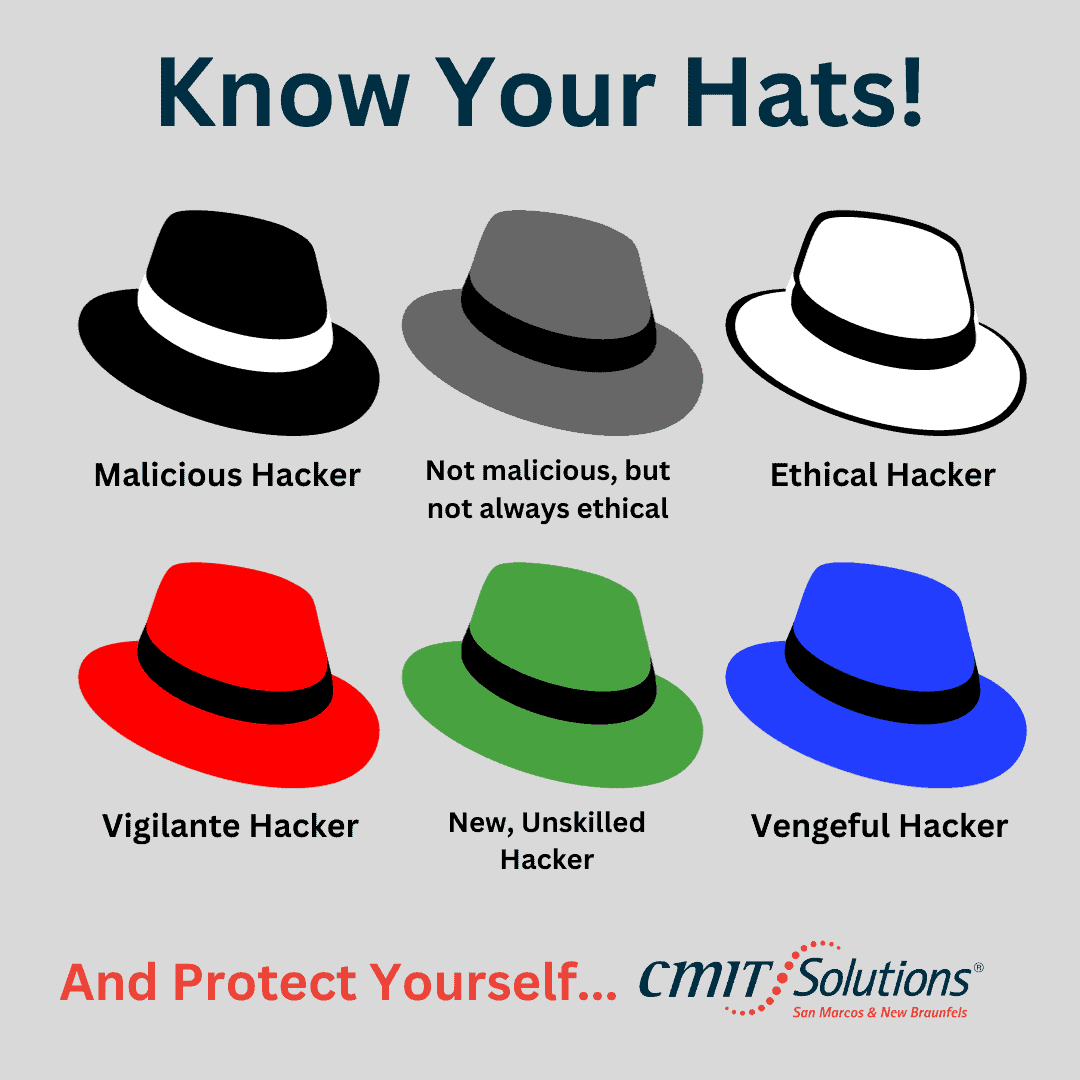
The world of hacking is a fascinating one, with a myriad of different personalities and motivations. To begin with, there are black hat hackers, who use their skills for illegal and malicious purposes. Contrastingly, there are the white hat hackers, who use their knowledge of computer systems for good, often employed to find and fix security flaws. The gray hat hacker is a bit of a hybrid, sometimes operating with good intentions, and other times crossing the line into criminal territory. Similarly, the blue hat hacker is often hired to test a company’s security system but can also be associated with cyber espionage. The red hat hacker is particularly dangerous, seeking to destroy systems and cause chaos. Finally, the green hat hacker is relatively new to the hacking scene and is often unskilled but eager to learn. As you can see, there’s a lot more to hacking than what meets the eye!
Motivation of Hackers
Hacking is vast, diverse, and ever-changing with many different individuals and groups utilizing their skills for various reasons. Some hackers may be motivated by a desire for money, looking to exploit vulnerabilities for financial gain. Others may be motivated by activism, seeking to expose injustices and promote certain causes. Still, others may simply be bored or seeking a challenge, looking to test their skills and push the limits of what they can accomplish. Regardless of their motivations, hackers remain a constant and ever-evolving presence in technology, shaping and influencing how we interact with and understand the digital world.
Tools and Tactics
In today’s increasingly digitized world, the threat of cyber-attacks is very real. Whether it’s personal data being stolen, or entire systems being shut down, the consequences of hacking can be severe. However, not all hackers are the same. There are various types of hackers, each with their own goals and methods. By being aware of these different types, individuals can better protect themselves and their information. For example, knowing about a white hat hacker can help individuals understand the security risks and take preventative measures, while a black hat hacker may exploit these vulnerabilities for malicious purposes. Overall, being aware of the different types of hackers is crucial for safeguarding against the risks of cybercrime and maintaining a secure digital presence.
How to Protect Yourself from Malicious Hacking Activity
To protect yourself and those around you from malicious activity, it’s crucial to use proper cybersecurity solutions such as encryption, firewalls, and antivirus software to ensure your data is safe. Additionally, log in using strong passwords, keep backups on secure servers, and change passwords regularly. Being tech-savvy and informed are essential steps for preventing security incidents. As hacking isn’t likely to disappear anytime soon, understanding the various types of hackers definitely helps us better protect ourselves online moving forward. Let’s all do our part in securing cyberspace by learning about all the different types of hacker classifications – black hats, white hats, gray hats, blue hats, red hats, and green hats. So, what are you waiting for? Learn all you can about these cybercriminals.
Why CMIT Solutions of San Marcos and New Braunfels?
Safeguarding your data is not something to take lightly or try to tackle alone. It requires a multi-layered and customized cybersecurity approach that evolves as new threats emerge. At CMIT Solutions of San Marcos and New Braunfels, we stay on top of the latest risks and solutions so you can focus on running your business. Our robust measures combine leading technology, security best practices, employee training, and diligent monitoring tailored to your unique needs and industry.
Don’t leave your livelihood exposed! Trust an expert team dedicated to cybersecurity. Reach out today and let CMIT Solutions lock down your data, detect threats early, and keep hackers at bay. With vigilance and a partner you can trust, you’ll gain peace of mind knowing your business is protected.