FAQs on Cyber Protection Solutions
Who Needs Cybersecurity Support?
Any business that stores or accesses sensitive data or financial information through digital means requires reliable cybersecurity solutions. Companies of all sizes face vulnerability to cyberattacks and must adopt proactive measures to protect their systems. Key protections include secure authentication methods, the use of trusted cloud storage, and investment in intrusion detection tools.
The most effective defense against cyber threats is a multi-layered cybersecurity strategy. This may involve penetration testing, real-time threat hunting, and cloud-based monitoring services that continuously oversee network activity. Adhering to information security best practices, such as enforcing encryption standards, removing unused accounts, and ensuring secure software updates, is critical to maintaining system integrity and long-term operational security.
With cyber threats evolving rapidly, from malware and spyware to ransomware targeting small businesses, organizations must stay updated on cybersecurity trends and technologies. By investing in employee training, advanced tools, and tailored security frameworks, businesses can reduce risk, prevent data breaches, and align with regulatory and cyber insurance requirements.
What Does Cybersecurity Support Include?
We deliver complete IT and cybersecurity services designed for businesses of all sizes. We recognize the growing risks posed by cyber threats and the vital importance of cybersecurity in today’s business environment. That’s why our cybersecurity support goes far beyond simply blocking attacks.
Our services include a wide selection of software tools that help safeguard sensitive data from theft and unauthorized access. We help businesses assess their exposure to risk, offer actionable guidance to reduce vulnerabilities, and ensure that security measures meet all relevant compliance standards and industry-specific requirements.
Since each business has unique security challenges and operational needs, we tailor our services to deliver the right level of protection. Whether it’s advising on firewall configuration, detecting malicious software, or managing user access and permissions, our team provides continuous cybersecurity support to keep your systems safe and running efficiently.
For companies seeking a safer IT environment and compliance with evolving data protection laws and frameworks, we offer the trusted expertise and advanced tools needed to defend against cyber threats with confidence and consistency.
What Do Cybersecurity Support Services in Tacoma Include?
We provide comprehensive IT services and cybersecurity solutions to businesses of all sizes. We understand the potential risk of cyber threats and the critical role that cybersecurity plays in any modern business. That’s why our cybersecurity support services include much more than just preventing cyberattacks.
We can assist with cybersecurity by providing a wide range of software products that help to protect confidential information from cyber activities and data theft. Our security solutions offer assistance in determining the extent of the risks and provide advice for mitigating threats, all while protecting company data under the necessary data compliance regulations.
We understand that every business faces different cybersecurity issues, so we offer tailored services to provide the highest level of security available. From advice on avoiding malicious software and implementing robust firewalls to user management, our experienced staff provides round-the-clock cybersecurity support to ensure your data remains safe.
For any business looking to secure its IT environment and comply with data protection regulations, our company has the solutions and services to get the job done. Our knowledgeable team and state-of-the-art tech give you peace of mind from cyber threats.
What Are the Most Important Components of a Cybersecurity Package?
As more businesses and organizations rely on digital systems, the potential for cyberattacks continues to grow. To stay protected, companies must adopt a comprehensive cybersecurity package that addresses both technical defenses and human factors. At CMIT Solutions, we emphasize the value of knowing each essential element that makes up a complete cybersecurity framework. These components help secure sensitive data, reduce business risk, and protect customer trust.
Below are the core elements we recommend including in any well-rounded cybersecurity solution:
- Data Compliance: Data compliance means following relevant industry laws and regulations. This includes using antivirus software, limiting data access, and keeping regular, secure backups.
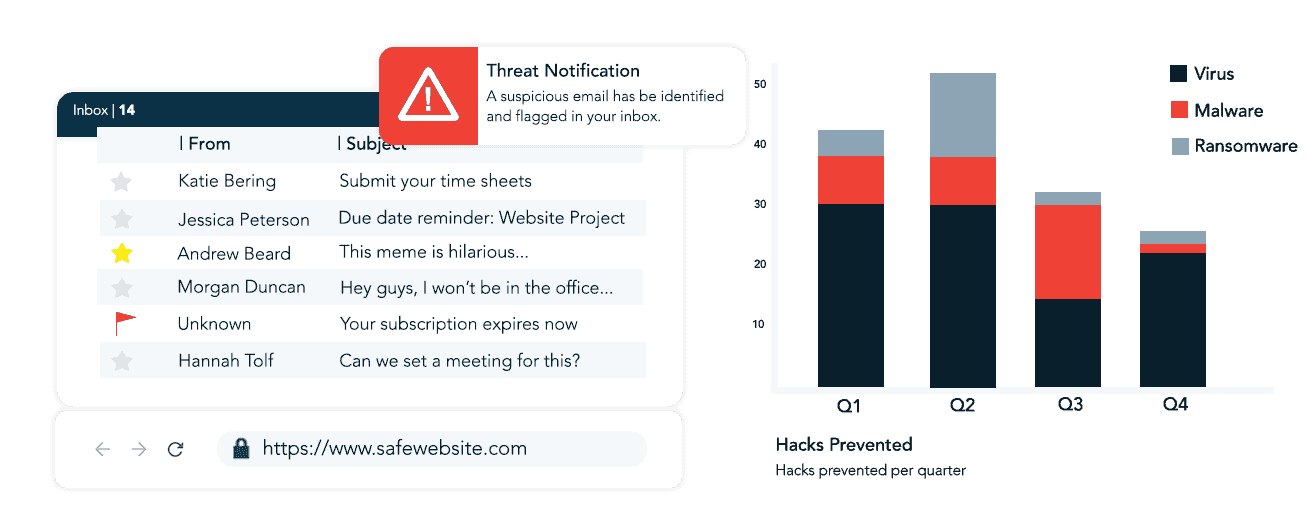
- Software Products: Using the right software tools helps prevent cyber threats. Examples include web filters, activity tracking programs, and email scanners that block suspicious messages.
- Cyber Threat Awareness: Employees should be trained to recognize cyber threats like phishing and weak passwords. Ongoing education and strong login policies reduce the risk of user error.
- Mitigate Potential Risk: Risk mitigation requires having clear plans to address any potential risk. This includes incident response procedures, data loss prevention steps, and periodic penetration testing.
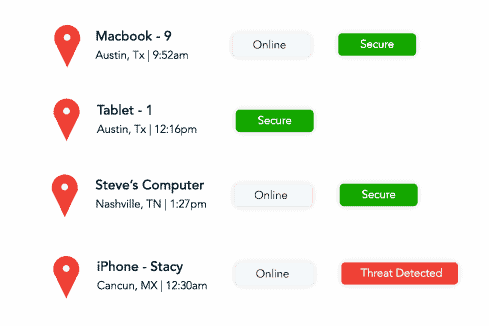
- Monitor Cyber Activities: Monitoring cybersecurity through a Security Operations Center (SOC) or Security Information and Event Management (SIEM) platform is a critical aspect of a strong defense posture. Establishing policies and deploying security tools to track and log all activity across networks, systems, and databases allows organizations to detect malicious behavior and respond quickly to potential cyber threats before damage occurs.