For most of us, emails are a fact of life. We receive them all day, we respond to them all day, and we write them all day. (We even work on emails at night and on the weekends, even though we probably shouldn’t). That constant pace and presence of emails mean phishing attempts continue to proliferate, turning our inboxes into a mix of legitimate messages and scary spam.
A phishing attack occurs when a hacker sends you an email that tries to convince you to perform a certain action. Phishing emails are effective because they look like regular emails and are hard to identify. The aim of phishing emails is usually to gather personal information about you, generally related to your login credentials, passwords, or finances. Many phishing attempts are often so well-disguised that they escape the scrutiny of a busy employee who doesn’t have time to closely inspect each message.
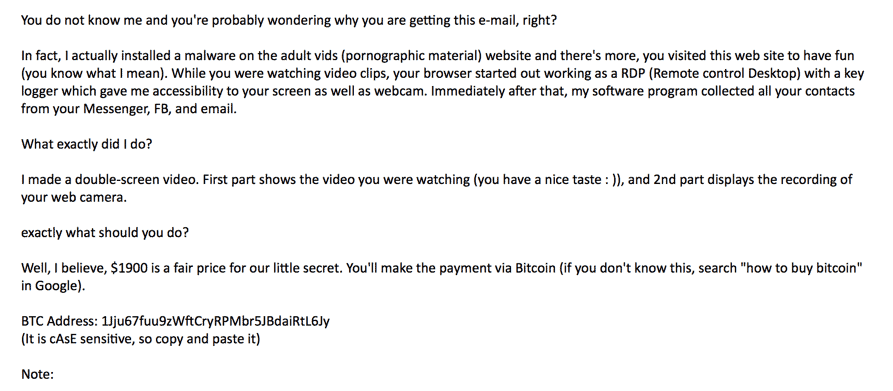
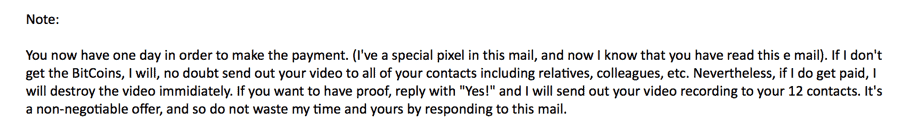
Lately, phishing attempts have taken on new attributes: fake FedEx tracking correspondences that look eerily real. Invitations to edit Google Docs that actually spam a sender’s contact list. And a scary new scam that claims to have used your webcam to record a video of you browsing illicit adult websites. That latter example even includes personalized information purporting to know one of your old email passwords—and threatening to release the incriminating video to your family and friends if you don’t pay a hefty Bitcoin ransom.
So how can you tell whether an email is legitimate or just another attempt at compromising your personal information?
An email might look like it’s coming from someone you know, but hackers can easily duplicate a display name while using a different address. Ask these questions if a message looks suspicious: were you expecting this email? Is the domain name correct? If you look closer by inspecting the details of the sender’s name, subject line, and body copy, you might find minor mistakes or strange phrasings that wouldn’t be found in a legitimate email.
Phishing emails tend to have a sense of urgency—hackers want you to feel rushed and make mistakes. Commonly used words to look out for include “ATTENTION,” “URGENT,” “CRITICAL,” “NECESSARY,” or “RESPONSE REQUESTED.” Spotting these anywhere in an email is your first hint that it could be a phishing attempt.
Is the email easy to read? Are there lots of errors? Are any sentences or phrases written so awkwardly that you have to go over them two or three times just to understand them? If so, use caution—any legitimate email will most likely be spellchecked before it’s sent. The new webcam scam that threatens to have incriminating evidence of your browsing history may start with a personalized message and even one of your actual old emails, but the rest of it reads like a clunky, incoherent stab at a phishing attempt.
Hover over the link to make sure it is correct before you even think of clicking on it—if the words say http://www.google.com, the preview link should also be http://www.google.com. Beware of long strings of nonsensical characters or any major differences between the link in the email copy and the preview link that shows up when you hover over it.
If you’re concerned about the authenticity of an email, DO NOT download any of its attachments as they could contain a virus that might install illicit malware or ransomware on your computer. In recent years, phishing attempts have employed ZIP files, PDF files, and even .WAV files masquerading as voicemails that are sent directly to your inbox. Clicking one of these infected files can cause widespread damage to your computer and any other systems it is connected to.
Company-wide Internet filtering and network security can stop some unauthorized phishing attempts. Employers should also take extra precautions to alert their employees when and from whom any critical communications will arrive. Also, notifying IT support staff—whether internal or external—when obvious phishing attempts do land in your inbox can also cut down on the future threat of fraud or infection. Even the best technology requires smart, savvy human beings whose insight and intelligence can help systems work properly.
The bottom line? Be careful out there! New phishing attempts emerge on a daily basis, and real security requires a proactive approach to protecting your email accounts. At CMIT Solutions, we worry about IT so you don’t have to, and our North American network of more than 200 locations and 800 technicians work 24/7 to prevent our clients from being negatively impacted by phishing attempts, scams, hacks, data breaches, malware, viruses, and more. Contact us today to learn more.