FAQs About Cybersecurity Solutions
Who Needs Cybersecurity Support?
Any organization that uses digital tools to manage sensitive data, financial information, or client records requires cybersecurity support. Regardless of size or industry, all businesses are vulnerable to cyber threats and must take proactive measures to protect their systems and data.
Effective protection starts with a multi-layered cybersecurity strategy. This may include identity authentication, cloud security, intrusion detection systems, penetration testing, and real-time threat monitoring. Companies should also follow industry best practices, such as strong encryption, disabling unused accounts, and ensuring secure software updates.
Cyber threats are constantly evolving, from viruses and spyware to ransomware targeting small businesses. To stay protected, organizations must stay informed, invest in employee training, implement modern security solutions, and comply with regulatory and insurance requirements.
What Does Cybersecurity Support Include?
Our cybersecurity support goes beyond simple threat prevention. We offer end-to-end protection tailored to meet the unique needs of your business.
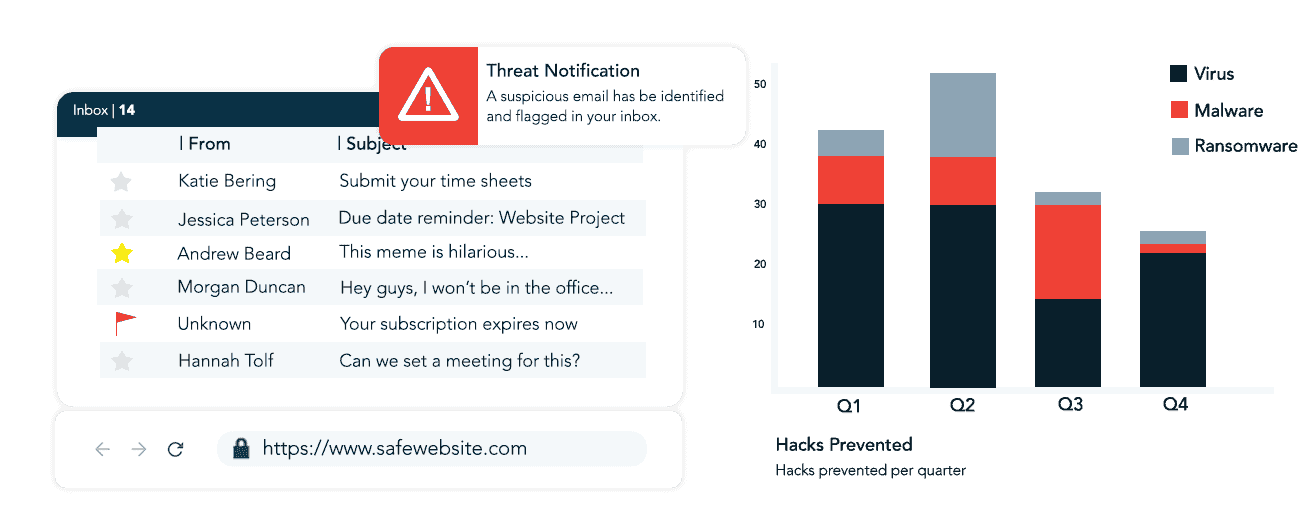
Our services include advanced software solutions to safeguard sensitive information, ensure compliance with data protection regulations, and minimize exposure to cyber risks. Whether it’s through malware protection, secure firewalls, user access management, or round-the-clock monitoring, our experienced team works closely with you to maintain a secure IT environment.
We also help identify vulnerabilities, mitigate threats, and respond quickly to incidents, providing both strategic guidance and technical expertise.
What Are the Core Components of a Strong Cybersecurity Package?
To combat today’s digital threats effectively, a comprehensive cybersecurity package should include:
- Data Compliance: Ensure your business meets regulatory requirements (e.g., HIPAA, PCI, GDPR) through proper data storage, encryption, and backup strategies.
- Advanced Software Tools: Use specialized software to block unsafe websites, monitor network activity, and filter out malicious emails.
- Employee Awareness Training: Educate your team on cyber risks, phishing scams, and password hygiene through ongoing training initiatives.
- Risk Mitigation Planning: Prepare for incidents with detailed response plans, data loss prevention strategies, and penetration testing.
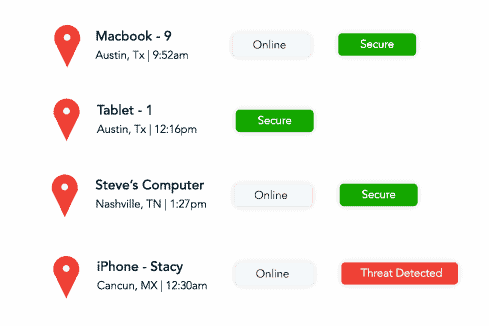
- Continuous Monitoring: Implement SOC and SIEM solutions to detect and respond to threats in real-time, ensuring comprehensive oversight across your systems and networks.
With these essential elements in place, your business will be better positioned to prevent attacks, protect data, and maintain operational continuity.