Cybercrime threatens businesses of all sizes, but small and medium-sized businesses (SMBs) are now the favorite target for hackers. Some small business owners might even wonder: Are small businesses really a target for cyberattacks?
The answer is a resounding yes, and unfortunately, they are increasingly the preferred target. This is because they often operate with limited resources and lack the robust defenses of larger corporations, making them appear as easy targets.
So, where should you start? Cybersecurity services providers—like CMIT Solutions—offer tailored solutions, making enterprise-grade protection accessible even for small businesses.
This guide will break down how budget-friendly business IT solutions can assist in implementing enterprise-grade cybersecurity—without breaking the bank.
Understanding the True Business Cost of a Cyberattack
Cybersecurity inaction carries staggering hidden costs far exceeding preventive measures. A single cyberattack paralyzes operations, causing immediate downtime that halts client services and revenue streams. Beyond the initial disruption, direct financial losses mount rapidly. Many small businesses lose tens of thousands from operational standstills alone.
In fact, the devastation proves so severe that 60% of small businesses completely shut down within six months of a major breach. However, the damage cascades further: irreparable reputational harm follows, eroding hard-earned trust.
Furthermore, breaches can trigger legal avalanches, with steep regulatory fines under laws like HIPAA or GDPR compounding the losses. At the same time, the theft of intellectual property—like trade secrets—can hand your competitive advantage directly to rivals.
Compounding these threats, investors now scrutinize security postures, making weak defenses a funding deal-breaker.
Ultimately, these interconnected risks reveal security not as an expense but as an essential business function. This shifts the conversation from whether you need protection to how to implement it affordably—a far more manageable challenge.
The following section dispels common myths about pricing and reveals why enterprise-grade security doesn’t require a big-business budget.
How Much Should A Small Business Pay For Cybersecurity?
Someone, somewhere, told small business owners that enterprise-grade cybersecurity is too expensive for them—a common belief rooted in the idea that only large corporations can afford top-tier protection.
But this perception doesn’t hold up—cybersecurity costs scale with your specific business risk, not the size of your organization.
The answer isn’t a fixed dollar amount, but rather a cost aligned with your unique vulnerabilities and the value of the data you protect. Enterprise-grade cybersecurity is akin to a flexible framework built around multi-layered protection, advanced threat detection, and continuous monitoring that work in concert.
Tailoring costs to their actual vulnerabilities and usage patterns enables small businesses to afford enterprise-grade cybersecurity. Instead of massive upfront investments, you adopt a pay-as-you-go approach where expenses align with your protection needs. Otherwise, pursuing expensive in-house security teams becomes a costly burden that most small businesses can’t shoulder.
However, it’s crucial to understand the shared responsibility model for cloud services. While providers secure their infrastructure, you must protect your data, access controls, and applications within it. This division of duties creates a comprehensive security posture where both parties contribute to your defense.
By embracing this model, enterprise-grade cybersecurity transforms from a cost center into a strategic advantage. Every security layer implemented holds the power to prevent breaches, avoid downtime, and preserve your reputation.
The following section outlines practical steps essential for building a strong cybersecurity foundation—your first line of defense.
What Cybersecurity Is Essential For A Small Business?
To build your strong defensive foundation, focus on implementing essential, high-impact cybersecurity practices that are affordable yet powerfully effective against evolving threats.

Prioritize these four critical steps:
- Implement Multi-Factor Authentication (MFA): This crucial first step blocks unauthorized access by requiring multiple verification factors. MFA strengthens security beyond passwords through additional layers, such as biometrics or mobile codes.
- Cultivate a Cybersecurity Culture Through Training: Since human error causes most breaches—especially phishing attacks—ongoing employee cybersecurity training and education transform your team into a vigilant frontline defense. It’s how small businesses afford enterprise-grade cybersecurity, turning staff into shields against social engineering while building a proactive cybersecurity culture.
- Enforce Strong Password Policies: Mandate complex, unique credentials using password managers—this fundamental control prevents credential-based compromises.
- Maintain Regular Data Backups: Ransomware attacks can encrypt critical data, but regular data backups (automated, off-site, and cloud) ensure restoration without ransom payments.
While these practices create a robust defense, managing them alongside advanced protections demands significant expertise and time—our next area of focus.
Also Read: Developing a Strong Cybersecurity Culture in Organizations: Your Complete Guide
Accessing Advanced Protection Through Managed Security Services
If you’re struggling with limited resources while trying to manage sophisticated security demands, continuing alone risks catastrophic breaches. This is where partnering with a Managed Security Service Provider (MSSP) becomes essential. Think of an MSSP as your dedicated cybersecurity services provider, offering outsourced expertise that fills critical skill gaps while managing your security operations.
Often delivered through Cybersecurity-as-a-Service (CSaaS), this flexible model provides pay-as-you-grow protection, eliminating the need for significant upfront technology investments and specialized hiring costs. You gain predictable, scalable expenses while avoiding the financial drain of maintaining an in-house team, freeing capital for core business growth.
Through this partnership, you access:
- 24/7 expert monitoring and rapid incident response
- Advanced enterprise tools like SIEM (centralized threat analysis) and XDR (cross-platform detection)
- Continuous security updates and vulnerability management
Moreover, compliance certifications like SOC 2 are achieved through rigorous documentation and controlled processes. This certification becomes a powerful trust signal that reassures clients about their data safety while strengthening your market reputation.
Ultimately, outsourcing to a managed service provider is the modern solution for accessing enterprise-grade protection affordably—a move that transforms security into your core strategic advantage.
Next, let’s explore how CMIT Solutions delivers enterprise-grade protection through a layered security approach built for small businesses.
CMIT’s Enterprise-Grade Cybersecurity With a Layered Approach
Most SMBs tend to think of cybersecurity as a simple/basic wall—perhaps an antivirus software or a firewall to guard their business. But enterprise-grade security is much more than that. It’s like a fortress with multiple layers of protection, like a moat, guards at each entrance, and an inner vault that protects your precious assets.
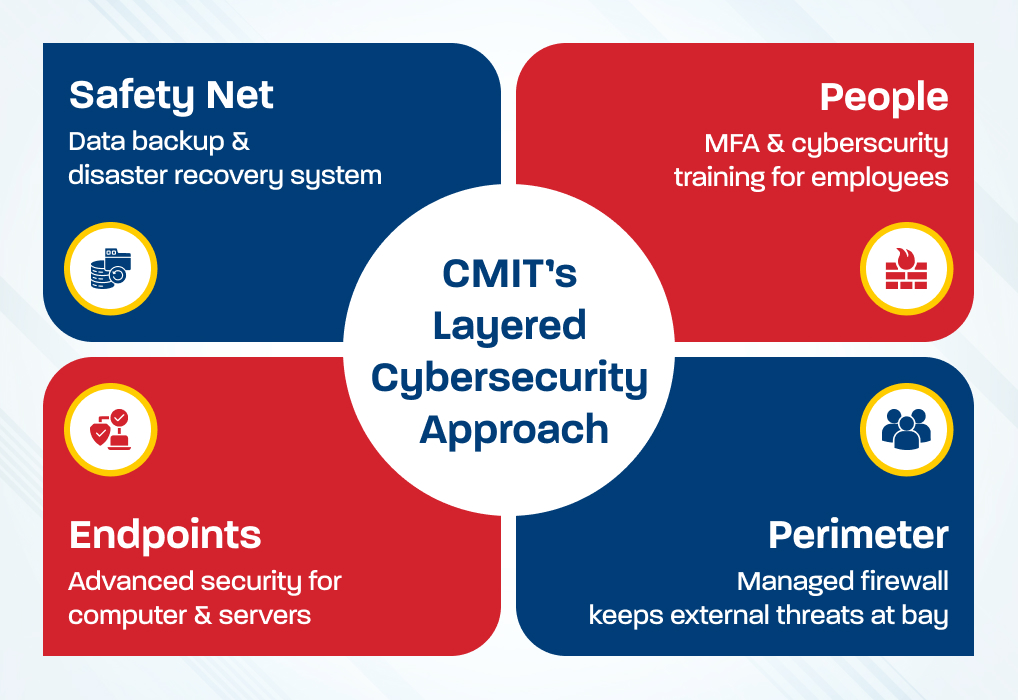
This is the layered approach to security, and that’s exactly how CMIT Solutions delivers enterprise-grade protection. Here are the four pillars that fortify your digital castle:
- Pillar 1 – The Perimeter (Your Moat): A professionally managed, actively monitored firewall that keeps external threats at bay.
- Pillar 2 – The Endpoints (Your Guards): Every computer and server in your organization is protected with advanced endpoint security.
- Pillar 3 – The People (Your Access Rules): MFA ensures access only for authorized personnel, while employee cybersecurity training helps staff recognize and respond to security threats.
- Pillar 4 – The Safety Net (Your Vault): A robust, regularly tested data backup and disaster recovery system to keep your most important information safe and retrievable.
Bridging the Solution: From Complex to Cohesive
For SMBs, independently managing all four of these layers can be overwhelming and expensive. As a managed service provider, CMIT Solutions helps solve this challenge. We offer a single, streamlined, and cost-effective service using the industry’s best practices and the latest tech tools.
Therefore, instead of piecing together cybersecurity on your own, you get an integrated shield managed by experts. This is how CMIT Solutions evolves from an IT vendor to being a reliable cybersecurity partner, navigating cybersecurity for your business.
Making Smart Cybersecurity Your Competitive Advantage
Enterprise-grade cybersecurity is no longer an optional luxury—but a vital and affordable necessity for small enterprises. Not only does this strategic investment build invaluable customer trust, but it also delivers a strong competitive advantage as privacy issues around data mount.
By taking a proactive approach to business risk management, you fortify operations against evolving threats while safeguarding your company’s longevity and credibility.
At CMIT Solutions in Silver Spring, we offer reliable and affordable business IT solutions to secure your company’s future. Connect with our team today to discuss your requirements and find budget-friendly, enterprise-grade cybersecurity solutions.




