Cybersecurity is often perceived as a purely technical domain — a battle fought with firewalls, encryption, and complex algorithms. However, this perspective completely overlooks a crucial truth: the human element remains the weakest link in the cybersecurity equation. While technology provides essential safeguards, it’s the actions, awareness, and diligence of humans that ultimately determine an organization’s resilience against cyber threats.
To strengthen this human element, implementing strong cybersecurity training and education is essential for organizations — especially smaller companies, as they are often targeted due to perceived weaker security defenses.
This guide explores how emphasizing the human element helps create an environment where security isn’t just a policy — but a continuous, collaborative way of working.
What is the Human Element of Cybersecurity?
The human element in cybersecurity refers to the complex interaction of:
- Human behavior
- Thought processes (cognition)
- Possible errors that can increase security threats — including data breaches
Rather than a weakness in itself, if well managed, the human factor can become an active and dynamic defense against cyber threats.
By recognizing the special abilities of the human element, investing in targeted training, and promoting a pervasive security awareness culture, organizations are able to close the gap between human decision-making and technological safeguards.
Next, we’ll look at how human errors influence cybersecurity outcomes.
How Human Error Impacts Cybersecurity
Critical human-related vulnerabilities are:
- Phishing Attacks — People are tricked into sharing sensitive data (passwords, usernames, financial information) through impersonating messages. Despite advancements in threat detection and email filtering, phishing persists because it exploits universal human vulnerabilities — such as trust, curiosity, and a sense of urgency.
- Poor Password Practices — Using weak, outdated passwords, reusing the same password across various sites, and not implementing Multi-Factor Authentication (MFA) are strong causes of security compromise. Due to a lack of awareness or convenience, people often overlook important security protocols.
- Social Engineering — Attackers psychologically manipulate individuals to perform actions they would not otherwise do, like clicking on a suspicious link or disclosing confidential information. Techniques involve impersonation or making something seem urgent.
- Insider Threats — Employees with access to confidential information may intentionally or inadvertently leak sensitive data or neglect security protocols, exposing internal weaknesses that can result in data breaches and financial losses.
- Negligence and Complacency — Employees may unintentionally reveal sensitive information by skipping simple security protocols. This involves ignoring regular software updates, connecting to unsecured Wi-Fi, or leaving computers unlocked or unattended. Lack of training and awareness can create a false sense of security.
Next, let’s uncover how human error amplifies cyber risks across businesses.
The Alarming Impact of Human Error on Cyber Risks
According to IBM’s Cost of a Data Breach Report 2025, the average cost of a breach globally now stands at an alarming $4.4 million. For small businesses, such an event can be catastrophic — humans are still identified as the “weakest link,” as human error contributes to an estimated 95% of cybersecurity incidents in small businesses.
Further insights from the 2025 Data Breach Investigations Report reveal that 60% of breaches involved a human element, ranging from phishing clicks to misconfigured security settings — a consistent trend across previous reports.
Breaches involving human interaction continue to account for the majority of cases.
Additionally, the 2025 Thales Cloud Security Study highlighted “The Liability that is the Human in the Loop,” noting that 68% of organizations cited stolen credentials and secrets as the fastest-growing cloud infrastructure attack tactics.
Supporting this, CyberArk’s 2024 research had already revealed that:
- 49% of employees reuse the same login credentials across multiple work applications.
- 36% use the same credentials for both personal and professional accounts.
- Worryingly, 65% of small and medium-sized businesses’ (SMBs) employees admitted to bypassing cybersecurity policies for convenience.
Next, we explore the hurdles to building stronger cyber awareness.
Also Read: Developing a Strong Cybersecurity Culture in Organizations: Your Complete Guide
Challenges in Cultivating a Security-First Culture
For SMBs, establishing a robust “security-first” culture presents several common hurdles:
- Resistance to Change — New security protocols can be perceived as inconvenient, leading to poor employee compliance.
- Limited Resources — A lack of dedicated IT staff and budget constraints often restrict investment in essential security tools and training.
- Knowledge Gaps — Without skilled experts, SMBs struggle to keep pace with the rapidly evolving landscape of cyber threats.
- Balancing Agility With Security — The pursuit of innovation and rapid business growth can sometimes inadvertently compromise cyber defenses.
However, these challenges can be effectively addressed through a strategic and prioritized approach — our next area of focus.
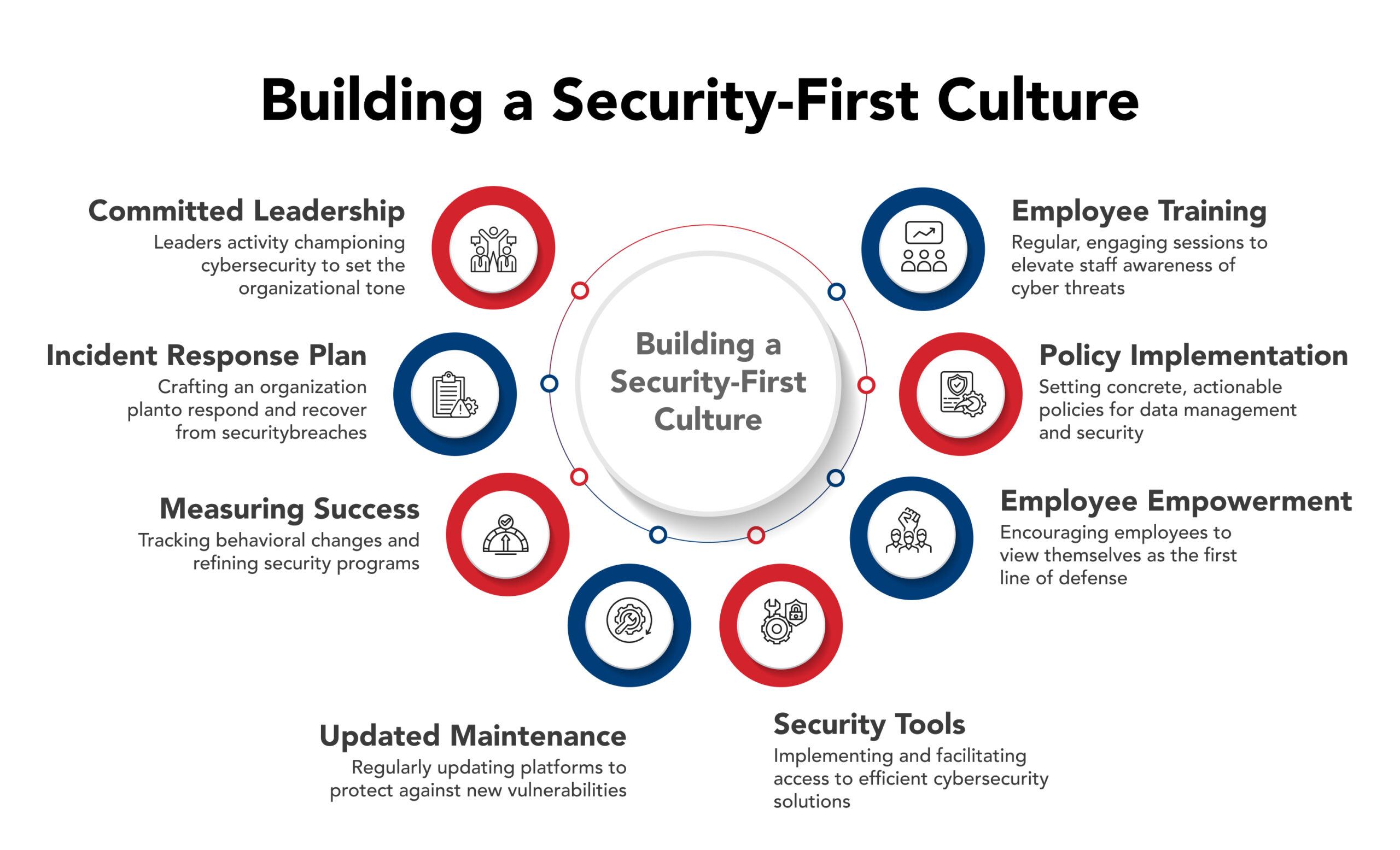
Key Strategies for Building a Robust Security-First Culture
Here are the essential strategies to implement:
Committed Leadership
When leaders actively champion cybersecurity, it signals its critical importance throughout the organization.
- Executives should not only advocate for security but also actively participate in training, adhere to protocols, and integrate security into strategic decision-making.
- This visible commitment sets the organizational tone and ensures the allocation of necessary resources, establishing security as a business priority — not an afterthought.
Comprehensive Employee Training and Awareness
Training should include:
- Phishing attempts identification
- Secure password practices
- Safe browsing habits
- Data protection protocols
Real-life scenarios, interactive sessions, and frequent updates on new cyber threats are crucial for reinforcing these concepts.
To ensure maximum impact, security training should be interactive, engaging, and relevant to employees’ daily roles and the specific threats they might encounter.
- Simulated Attacks — Phishing simulations are an effective means of evaluating employee awareness in a protected, controlled environment. They expose weaknesses and support targeted training.
- Gamification — Adding gamified modules and using rewards can transform training into a fun experience and reinforce positive security behavior.
- Microlearning — Providing brief, effective lessons as part of daily work processes keeps security concepts at the forefront.
Clear Policy Implementation
This includes setting concrete, actionable policies for employee behavior in managing and safeguarding data.
Policies must address:
- Password management
- Internet usage
- Sensitive information handling
Regular review and updating of these policies are essential to ensure they remain relevant and effective against evolving cyber threats.
Empowering Employees as Security Advocates
Employees should be empowered to view themselves as the first line of defense against cyber threats.
- Encourage them to report any suspicious activities immediately — such as unusual system behavior or emails.
- Reinforce this sense of empowerment and responsibility through open communication channels, regular feedback, and recognition of their vital role in maintaining cybersecurity.
Strategic Investment in Security Tools
Key cybersecurity tools for protecting sensitive data include:
- Firewalls
- Antivirus software
- Intrusion detection systems
Ensuring these tools are accessible to employees and user-friendly is critical — enabling employees to use these tools effectively in their day-to-day operations.
Consistent Updates and Maintenance
This proactive approach ensures security controls are up to date and functional — minimizing the likelihood of cyberattacks substantially.
The process involves:
- Regularly updating all platforms with the most recent security patches to protect against newly found vulnerabilities.
- Regular maintenance audits for determining and correcting any prevailing security vulnerabilities.
Measuring Success and Continuous Improvement
Leaders should focus on measuring real behavioral changes — beyond just tracking training completion rates.
Key Performance Indicators (KPIs) include:
- Phishing reporting rates
- Decreased security incidents
- Positive feedback from employee surveys
By regularly tracking and refining the security program, organizations can anticipate threats ahead of time and keep their “human firewall” strong.
Comprehensive Incident Response Plan
The actionable response plan should outline near-term actions post-breach, such as:
- Identifying and containing the breach.
- Assessing the damage.
- Notifying stakeholders as appropriate.
The plan should also include:
- Procedures for systems and data restoration
- Lessons learned to improve future response
Through integrating these strategies into fundamental operations, small businesses can create an impenetrable shield against cyberattacks and develop an environment in which cybersecurity is a shared, collective responsibility.
Turning the Human Element Into Your Strongest Defense
By moving beyond technical defense and truly investing in a “security-first culture,” organizations can turn their employee base from a liability into their greatest strength.
An active cybersecurity culture:
- Empowers employees with knowledge.
- Makes employees aware of their own role in defending sensitive information.
- Encourages best practices.
Ready to establish a workforce that proactively supports cybersecurity strength? At CMIT Solutions, we offer comprehensive IT services — from customized risk assessments to extensive awareness training — to help businesses in Chevy Chase and Silver Spring invest in a security-driven culture. Connect with us today — safeguard your assets, stay compliant, and keep ahead of threats!
CMIT Solutions of Silver Spring isn’t just for businesses in Silver Spring! We extend our comprehensive IT services, cybersecurity expertise, and dedicated support to clients in the surrounding areas. Empower your operations in Rockville, Derwood, Chevy Chase, Olney, Burtonsville, and Highland with our reliable technology solutions.