As 2025 is coming to an end, identity and access threats continue to be a major concern for businesses. Businesses are increasingly relying on cybersecurity services to manage Identity and Access Management (IAM), as the numbers highlighting these risks are astounding.
According to IBM’s Cost of a Data Breach Report 2024:
- The average data breach costs climbed to $4.88 million, up from $4.45 million in 2023 (10% spike) — the highest increase since the pandemic began.
- For the second consecutive year, phishing, stolen, and compromised login credentials were the top causes of breaches and also among the most expensive types of incidents.
Though these statistics underscore enterprise-scale risks, small and medium businesses (SMBs) face equally alarming realities.
A Microsoft Cybersecurity survey discovered that 1 in 3 SMBs had been a victim of a cyberattack over the previous year, and the average cost of each attack was $255,000. This statistic reveals that even smaller enterprises are not immune to identity and access threats.
This article explores how IAM:
- Protects sensitive information.
- Ensures compliance.
- Supports secure operations.
What is IAM and Its Purpose?
Identity and Access Management (IAM) refers to a set of policies, procedures, and technologies aimed at ensuring that the right employees, clients, contractors, partners, and machine identities gain access to the right resources at the right times for the right reasons.
IAM offers a robust strategy for multiple purposes:
- Verifying user identity
- Assigning access rights
- Assuring security standard compliance
- Managing and controlling user access to sensitive applications, data, and systems
With diligent IAM in place, organizations can:
- Establish foolproof security protocols.
- Enhance visibility across the entire infrastructure.
- Streamline all workflows.
Next, we’ll dive into the elements that make up IAM — highlighting the features and practices that protect your organization’s digital assets.
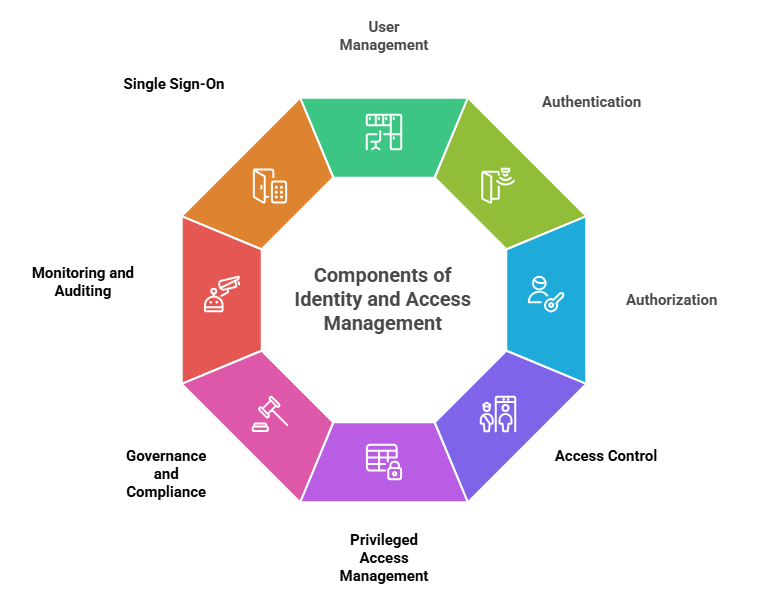
What is Included in IAM?
Here’s a closer look at what comprises IAM:
- User or Identity Management: Includes systematic user account and job role creation, assignment, deactivation, and maintenance in the organization — with the correct employee having the correct access.
- User Authentication: Authenticates a user or system as being the person who claims to be, employing tools such as passwords, biometrics, and Multi-Factor Authentication (MFA) to add strength to security.
- User Authorization: Specifies what resources a user is authorized to access and actions they may take once they have been authenticated — assisting in maintaining security over sensitive information.
- Access Control: Defines and enforces policy that dictates how users engage with digital resources — assuring that they have the minimum level of access needed to effectively perform their job without compromising security.
- Privileged Access Management (PAM): Concentrates on management and monitoring of users with higher privileges — e.g., system administrators — that guarantee proper security controls are enforced for these high-access accounts.
- Governance and Compliance: Implements processes, policies, and audit trails that enforce compliance with multiple security and privacy laws — assisting organizations in accessing the intricate web of compliance requirements.
- Monitoring and Auditing: Monitors login attempts and access requests and detects unusual behavior — enabling organizations to actively identify potential insider threats or misuse of credentials.
- Single Sign-On (SSO): Enables users to access multiple applications and services using one set of credentials — streamlining their experience while keeping security strong.
In the next section, we’ll examine IAM’s place within cybersecurity.
Also Read: Why SMBs Should Adopt an Enterprise Mindset in Cybersecurity
Is IAM Part of Cybersecurity?
Of course, IAM is very much a “fundamental” part of cybersecurity — fortifying your business’s security with the following measures:
- Preventing unauthorized access with strong authentication and access controls — to hinder users from violating sensitive information.
- Monitoring user activity in real-time — to identify credential abuse and malicious intent by tackling insider threats.
- Implementing centralized access controls — to enhance security in multi-cloud and hybrid environments.
- Managing the deployment of security best practices — to comply with regulations under HIPAA, GDPR, and other regulations.
So, what are the key components that make IAM essential for business security? Let’s break them down next.
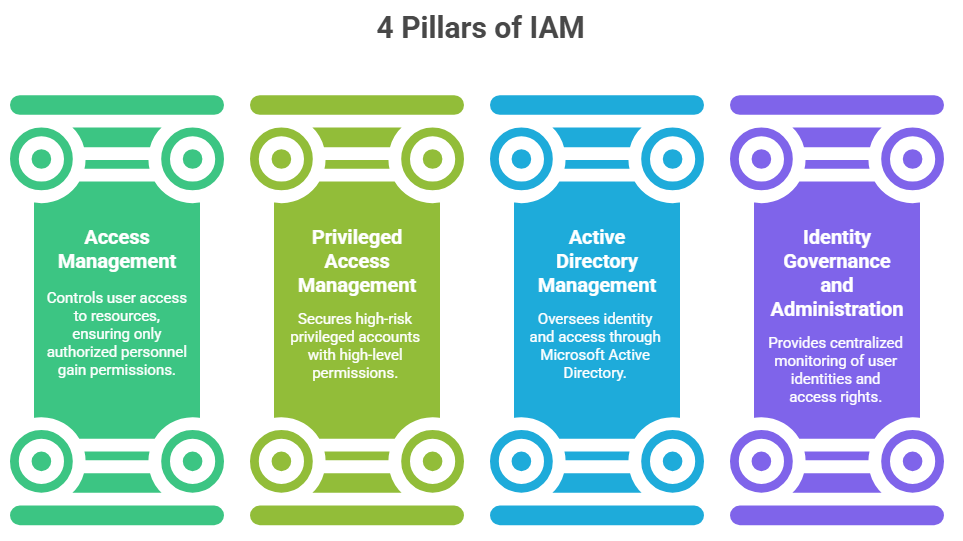
What Are the 4 Pillars of IAM?
IAM serves as an integrated framework, focusing on four essentials:
1. Access Management (AM)
Controls how users gain access to critical resources — ensuring that only authorized personnel are granted permissions.
Key features include:
- Management of centralized roles and permissions
- Support for multiple authentication protocols
- Role-Based Access Control (RBAC) for tailored access
- MFA for enhanced security
- Temporary privilege assignments for special circumstances
2. Privileged Access Management (PAM)
Focuses on securing high-risk privileged accounts with high-level permissions.
Key features include:
- Centralized oversight of privileged accounts and credentials
- Fine-tuned access permissions adhering to the least privilege principle
- Customized approval workflows for sensitive operations
- Automated password management (rotation) for stronger security
- Monitoring and auditing sessions for accountability
3. Active Directory Management (ADMgmt)
Oversees identity and access through Microsoft Active Directory — applicable to both on-premises and cloud environments.
Key features include:
- Integration with cloud identity providers for seamless access
- Automated onboarding and offboarding of users and groups
- Comprehensive monitoring, auditing, and reporting tools
- Enforcement of RBAC
- Protection against unauthorized access and misconfigurations
4. Identity Governance and Administration (IGA)
Provides centralized monitoring of user identities and access rights related to compliance and security.
Key features include:
- Automated workflows for user provisioning and de-provisioning
- Effortless integration with enterprise directories and systems
- Effective entitlement management and periodic access reviews
- Enforcement of Segregation of Duties (SoD) policies to mitigate risks
- Advanced analytics and reporting for compliance
Next — a closer look at the numbers and trends driving the IAM landscape.
Valuable IAM Statistics and Insights
Explore key IAM statistics, market trends, and security insights for businesses.
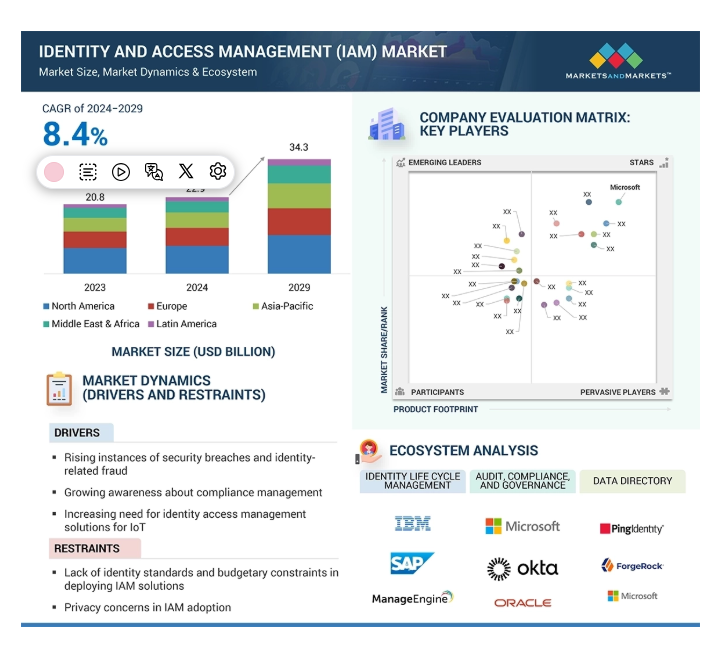
IAM Market Overview
The MarketsandMarkets report estimated the global IAM market size at $22.9 billion in 2024. This figure is projected to rise to $34.3 billion by 2029, reflecting a CAGR of 8.4%. This growing percentage presents a valuable opportunity for B2B organizations to enhance their user experience and streamline identity management across various platforms.
SMB Adoption and Awareness Gap
Despite the market growth, adoption among SMBs remains limited. According to a study, only 17% of small businesses use centralized IAM solutions, leaving most organizations vulnerable to credential theft and unauthorized access.
The CrowdStrike State of SMB Cybersecurity Survey also found that while awareness of cyber threats is high, actual implementation of IAM and MFA remains low due to outdated tools and limited resources.
Security Lapses Fueling the Demand for IAM Solutions
Research indicates that over 80% of data breaches are attributed to the use of stolen, default, or weak passwords. When IAM successfully enforces structured credential management, it significantly prevents users from relying on risky passwords and mitigates the likelihood of security incidents.
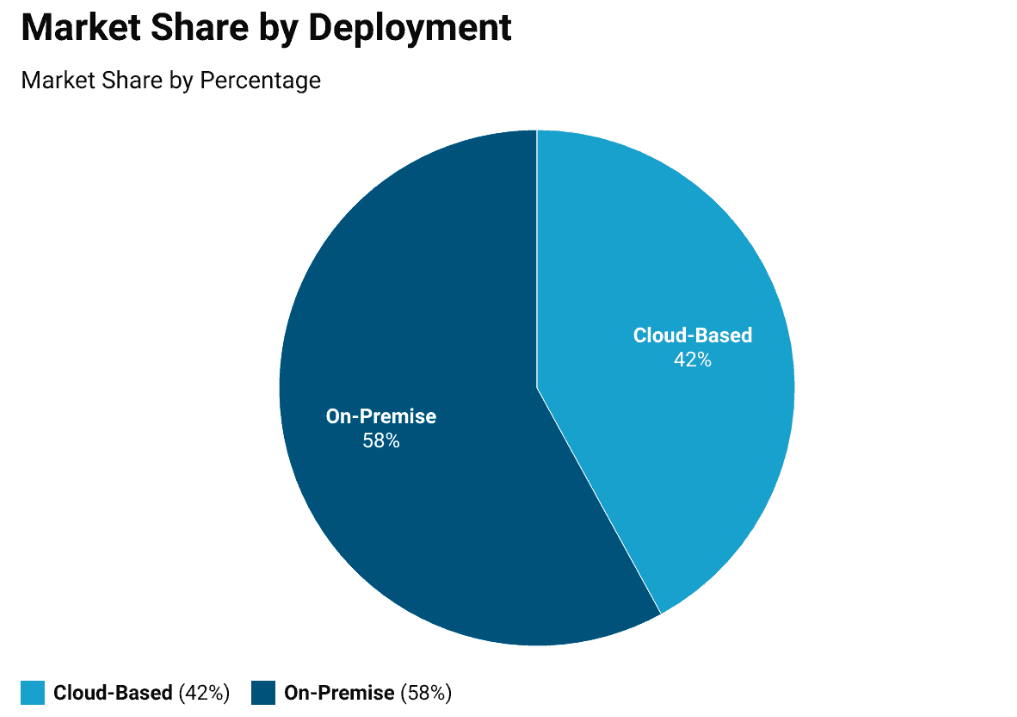
Deployment-Based Global Market Share
The global IAM market is experiencing a remarkable shift in deployment strategies. Currently, a substantial 58% of IAM solutions are installed on-premise, while cloud-based options are making impressive strides, capturing 42% of the market. This growing trend highlights its scalability, cost-effectiveness, and flexibility.
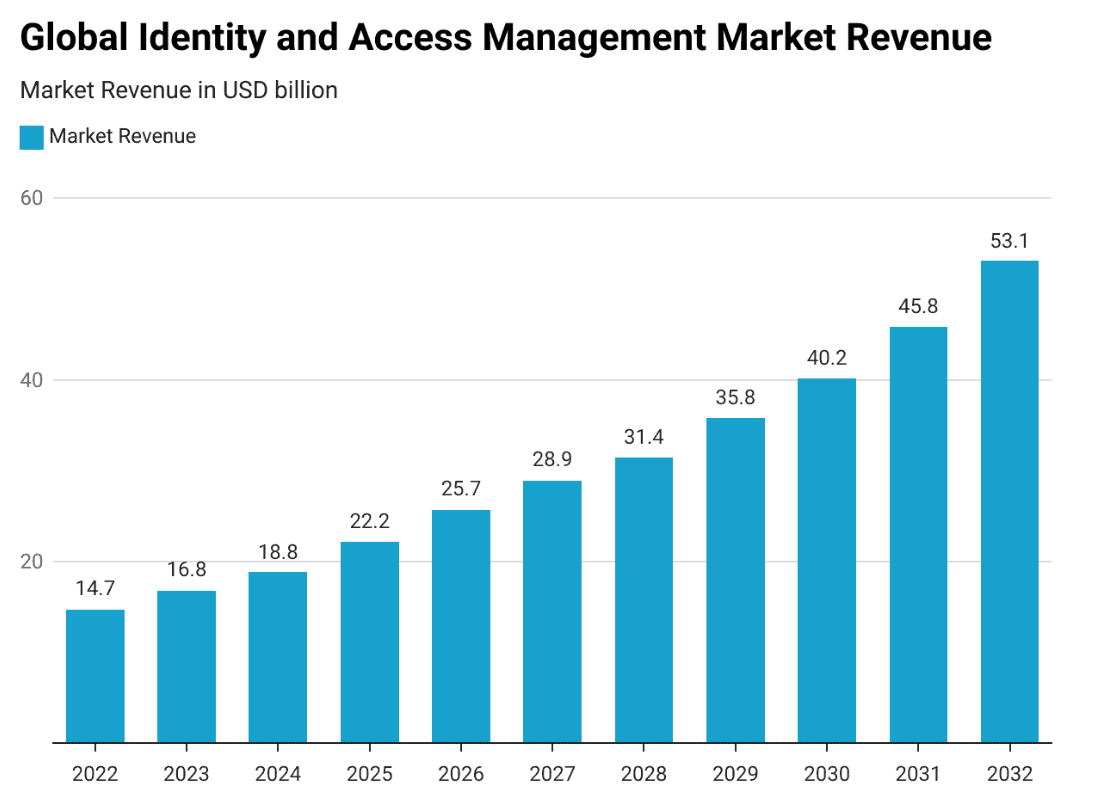
The Future of the Global IAM Market Revenue
Exciting times are ahead for the IAM market, with revenues projected to soar from $25.7 billion in 2026 to a staggering $53.1 billion by 2032. This remarkable upward trend highlights the crucial role of IAM solutions in enabling robust security and seamless access across the digital landscape.
In the following section, we’ll outline key practices to strengthen your IAM framework.
Developing an IAM Strategy: Best Practices for Organizations
Organizations seeking to enhance their IAM frameworks should adhere to these practices:
- Identify and fulfill all regulatory, industry, and operation-based requirements to align your IAM efforts with business risks.
- Upgrade your user access security with MFA strategies — such as biometric access, passkeys, and tokens.
- Create complex and unique passwords and encourage the use of password management tools for all access points.
- Apply the principle of least privilege and RBAC to assign access rights specific to each role and lock privileged accounts using PAM.
- Protect all computing devices — including laptops, desktops, mobiles, tablets, servers, and IoT — and endpoints with strong firewalls, device management platforms, and anti-malware tools.
- Strengthen email communication security with SEG (Secure Email Gateways) to counter phishing, business email compromise, and malware.
- Develop an employee IAM culture through consistent, formal training to reduce human error and create security.
- Automate IAM processes — including onboarding, role provisioning, and offboarding — to reduce potential risks.
- Run scheduled audits to refresh and track access entitlements and IAM policies to remain proactive against novel threats.
SMBs specifically need to leverage managed services and automation to fill gaps created due to limited budgets and smaller internal teams. Having explored these practices, let’s now look at what to anticipate in the upcoming years — as IAM evolves.
The Future Trends in IAM
Here’s what to expect in the near future:
- AI-driven automated decision-making, user behavior anomaly detection, and real-time adaptive access controls
- Ongoing verification (zero-trust architecture) for every user, system, and device — irrespective of their geographic location
- Enhanced flexibility, scalability, and centralized management across on-premises, hybrid, and multi-cloud environments
Building Stronger Security With IAM
IAM goes beyond being merely a security tool — it serves as the foundation for contemporary cybersecurity strategies to:
- Protect digital assets from unauthorized access.
- Maintain compliance with regulatory standards.
- Enhance operational efficiency and resilience.
For SMBs who commonly believe they’re “too small to matter,” the truth is otherwise — they have become increasingly prime targets for cyberattacks, with similar dangers previously reserved for large businesses.
At CMIT Solutions, we recognize that IAM is fundamental to a robust IT infrastructure. For businesses in Chevy Chase, our IT services are designed to develop and manage proactive IAM strategies. We also serve in Silver Spring and the surrounding areas with comprehensive IAM solutions.
Connect with us today to stay ahead of emerging threats and confidently prepare for the future!