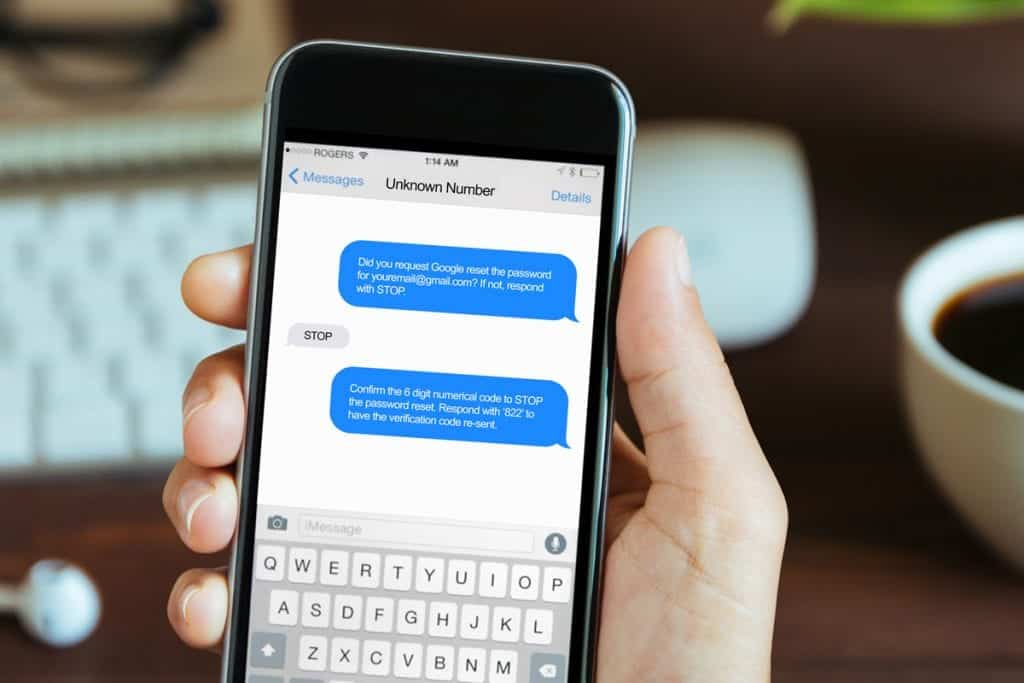
As cybersecurity threats multiply each week, a new version has cropped up—and many are claiming it’s the cleverest yet. This phishing scam works to try and throw a wrench in two-factor authentication, considered by many a necessary extra layer of password security.
Here are the details of the scam: a potential victim will receive a text message inquiring about a recent request for a Gmail password reset. The exact text reads, “Did you request Google reset the password for youremail@gmail.com? If not, respond with STOP.” That last line can fool almost anyone into responding, after which the scammers will say, “Confirm the 6-digit numerical code to STOP the password reset. Respond with ‘822’ to have the verification code re-sent.”
This is textbook social engineering—defined as “the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes.” With this tactic, scammers are increasing their chances of receiving a legitimate Gmail verification code (which they have requested for your email address).
If shared, that simple six-digit code could allow those hackers access to endless Google-associated accounts, changing passwords and stealing private information with impunity. Remember—Gmail or other web email services will never ask you if you DON’T want to do something with your account.
If you didn’t specifically request a password reset, don’t trust any communication that implies you did. If you do receive what you think might be an illicit request for passwords, verification codes, or other private information, don’t respond and report it to the service’s customer service department, or to a trusted IT provider. In addition, with this particular scam, DO NOT reply to the text message—doing so will let the scammers know that they have reached a valid cell phone number.
Plenty of choices exist for the type of second-factor authorization to set up. Your smartphone is the most ubiquitous and easiest-to-use option, with Touch ID becoming a common way to log in to important apps. Google, PayPal, and many banking institutions employ codes sent to you via text message or voicemail that you then enter to confirm your identity.
CMIT Solutions’ philosophy on IT service is proactive, not reactive: we monitor our clients’ systems 24/7 so that we can identify, prevent, and resolve issues before they affect productivity, efficiency, and security, not after they’ve already incurred downtime. From firewalls to antivirus, anti-spam, and anti-malware software to data encryption, content filtering, employee training, and other targeted tools, we believe the “umbrella” approach gives businesses the best chance to stay secure.
We’ve said it before, and it bears repeating: every employee, workstation, and mobile device represents a possible vulnerability. Most high-profile cybersecurity attacks are the result of coordinated hacking efforts, but many smaller ones stem from a lost password, stolen thumb drive, or inadvertently opened email attachment.
Guess what? It probably does. How long could your business operate without its critical information? How quickly would you need it to be recovered to bounce back from a catastrophic event? Studies show that backup and disaster recovery are integral to business success—the Small Business Administration estimates that 45% of companies that suffer from data loss never recover.
Recent reports indicate that one in three Americans have had their health records compromised without even knowing it. That means hackers are working harder than ever to steal sensitive information, especially in the healthcare realm, where one stolen record can sell for far more on the black market than a stolen credit card.
CMIT Solutions provides responsive, professional IT support and technology services for your business, performing regular ongoing maintenance, monitoring, and backups—everything necessary to ensure an efficient, safe, and reliable IT environment. If you’ve been targeted by a phishing scam or are unsure about the security of your information, contact us today.