Who Needs Cybersecurity Support?
Any business utilizing digital technology to store or access sensitive data or financial records requires cybersecurity solutions, especially here in CMIT Charleston. Companies of all sizes are vulnerable to cyber threats and must proactively defend against them. This defense should involve implementing authentication procedures, leveraging cloud storage platforms, and investing in intrusion detection systems.
Multi-layered cybersecurity solutions offer the strongest protection against the destructive impact of cyberattacks. An effective cybersecurity strategy may encompass penetration testing, threat hunting, or cloud-based services that monitor systems and networks. Adhering to information security best practices, such as proper encryption protocols, deactivating unnecessary accounts, and ensuring secure software updates, is crucial for businesses aiming to remain resilient against cyber threats.
As cyber threats continuously evolve, from viruses to ransomware, staying informed about the latest developments in cybersecurity is essential. Businesses should invest in the appropriate equipment, training, and security measures to safeguard their data. By embracing security best practices and investing in tailored solutions, companies can mitigate data loss, reduce cyber risks, fulfill insurance requirements, and comply with regulations.
What Does Cybersecurity Support Include?
At CMIT Charleston, we offer comprehensive IT services and cybersecurity solutions to businesses of all sizes. Recognizing the potential risks posed by cyber threats, we understand the pivotal role cybersecurity plays in modern business operations. That’s why our cybersecurity support services extend beyond mere prevention of cyberattacks.
We provide a range of software products designed to safeguard confidential information from cyber threats and data breaches. Our security solutions help assess the extent of risks and offer advice on threat mitigation, all while ensuring compliance with data protection regulations.
Understanding that each business faces unique cybersecurity challenges, we offer customized services to deliver the highest level of security. From guidance on avoiding malicious software to implementing robust firewalls and managing user access, our experienced team provides round-the-clock cybersecurity support to uphold the integrity of your data.
For businesses seeking to fortify their IT environments and comply with data protection regulations, CMIT Charleston offers the solutions and services needed for peace of mind against cyber threats.
What Are the Most Important Components of a Cybersecurity Package?
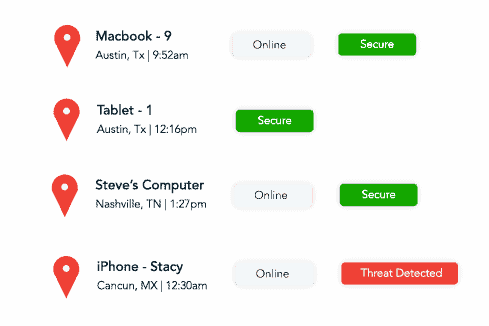
As the potential for cyber threats continues to grow, comprehensive cybersecurity solutions are crucial for businesses and organizations, particularly here in CMIT Charleston. Understanding the key components of such a package is vital for protecting data and ensuring customer safety.
In our view, the most critical components of a comprehensive cybersecurity package include:
- Data Compliance: Ensuring compliance with relevant laws and regulations, including installing antivirus software and maintaining data backups.
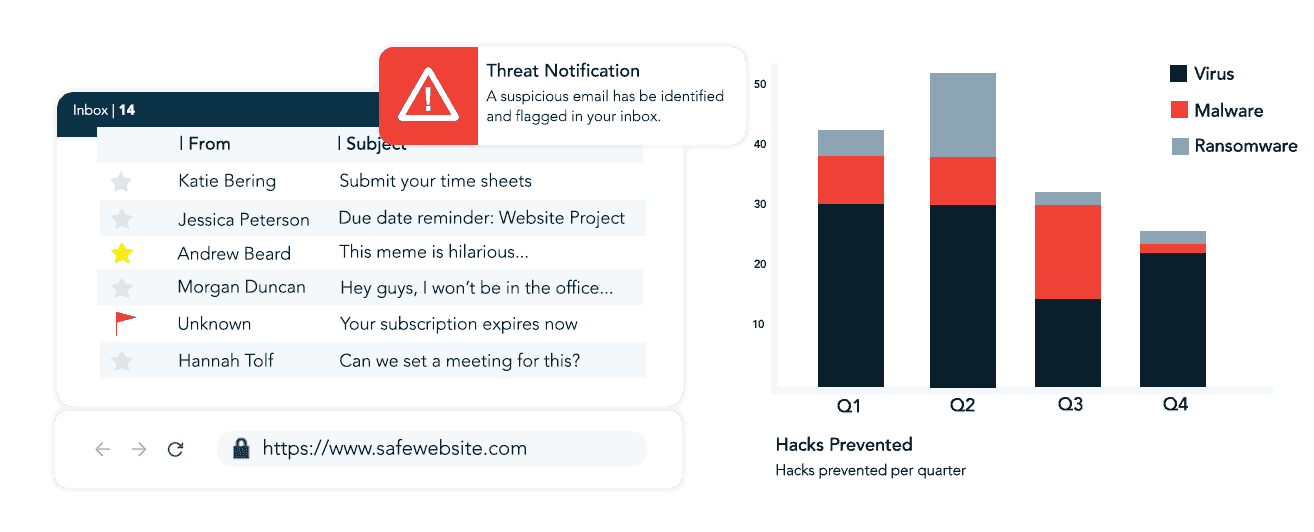
- Software Products: Implementing tailored software solutions to defend against potential risks, such as blocking access to malicious sites or detecting suspicious email messages.
- Cyber Threat Awareness: Educating employees and customers about potential threats and how to mitigate risks, including awareness of phishing attempts and adherence to strong password policies.
- Risk Mitigation: Developing plans to address potential risks in the event of a cyberattack, including incident-response planning and data loss prevention policies.
- Cyber Activity Monitoring: Utilizing Security Operations Center (SOC) or Security Incident and Event Monitoring (SIEM) services to monitor and log all activities on the organization’s networks, systems, and databases to identify and prevent cyber threats.
By prioritizing these components within their cybersecurity strategy, businesses in CMIT Charleston can better protect their data and operations from cyber threats.


 Managed Services
Managed Services
 Cybersecurity
Cybersecurity
 Productivity Applications
Productivity Applications
 IT Support
IT Support
 Cloud Services
Cloud Services
 Network Management
Network Management
 Compliance
Compliance
 Data Backup
Data Backup
 Unified Communications
Unified Communications
 IT Guidance
IT Guidance
 IT Procurement
IT Procurement