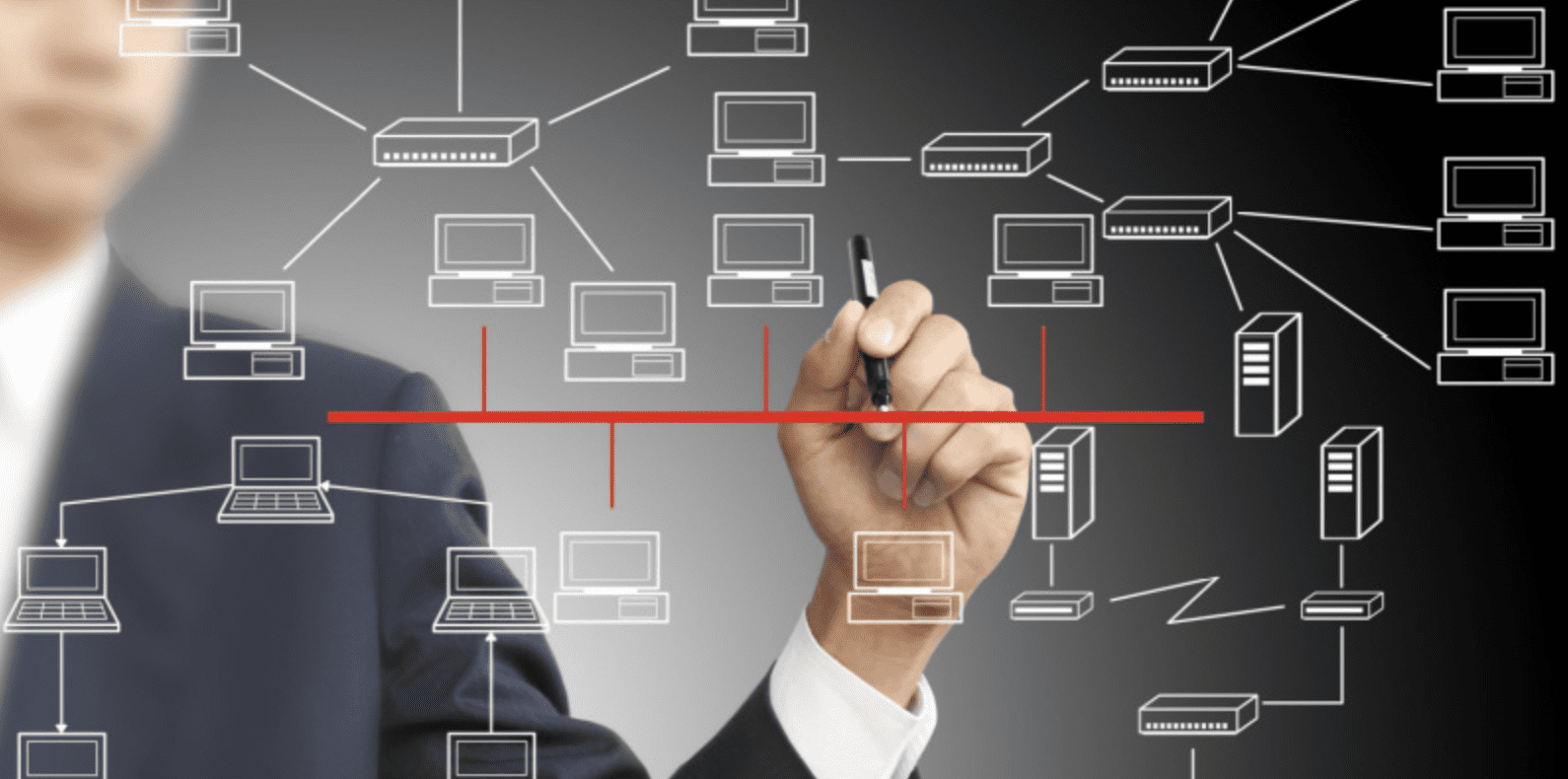
What do you think is the digital lifeline of most businesses in today’s modern world? It is your network- that undeniably complex tangle of workstations linked to constantly blinking routers, hubs, switches, and serves that create an invisible connection with the Internet.
Your network is like the brain, which is no exaggeration because here’s where everything happens. Metaphorically speaking, like how the skull protects the brain, your network needs an arsenal of security features like firewalls, virus filters, and Virtual Private Networks to keep it running without a hitch. All this calls for effective “Network Management.”
Let’s get straight to the point.
Network Management – What Is It & Why Is It Important?
Network Management is an entire system of tools, methodologies, protocols, and applications created to aid the operation, administration, and maintenance of your organization’s network infrastructure.
This system orchestrates the collection and analysis of network data to determine the following:
- Configuration changes required to maximize availability
- Changes to improve network performance
- Ways for better reliability and security
So, why is network management a prerequisite? Firstly, network management has always been at the top of the priority list and has become almost mandatory in the wake of the pandemic. Today’s network is a buzzing live wire carrying massive amounts of data in the form of voice, video, and content. Data is being shared back and forth between users non-stop. Furthermore, with digitization taking the world by storm and the increasing number of BYOD users, the enterprise network has become increasingly complex and difficult to manage.
Done well, network management delivers some noticeable benefits for your organization. One of the prime benefits is your network’s increased security and efficiency. With better efficiency comes reduced downtime because there are fewer unplanned technical glitches. This combined benefit results in the following:
- Better work flexibility
- Reduced unplanned outages and downtime
- Improved network efficiency
- Refined network modifications
- Increased ROI from network infrastructure investments
Is network management easy? Well, it is like juggling many things at once. You must embrace innovative technologies to stay abreast of the race and ward off cyberattacks at every entry point. These initiatives must be meticulously executed while providing a consistent, high-quality user experience. To make everything work in unison, you need some network management best practices.
Here are some best practices to get the most out of network management and gain that competitive edge.
10 Ways to Refine Your Network Management
1. Know your network
When it comes to your enterprise network, you ought to know these four aspects like the back of your hand:
- Your network’s topology
- The network type.
- The OSI model.
- The network devices.
These are the main components that keep your business alive and kicking. A solid understanding of the design, setup, and flow of data will allow you to build a strong and efficient network, troubleshoot problems quickly, and develop effective security controls.
2. Know your compliance standards
The more intricate your enterprise network, the more necessary it is to remain compliant with the rules and regulations. Even if you do not belong to mainstream organizations like healthcare and finance, who and where do you collect data from matters? In this context, remaining oblivious to network compliance standards could become a grave mistake, as your network is the gateway to all your resources. Compliance is challenging, but there can be no room for compromise. So, know your compliance standards and stick to them.
3. Know your network defenses
The next step is to learn about your network defenses, such as the security controls currently in place and the ones available. Identify the critical devices, systems, and software that form the core of your network infrastructure. Identifying which components need to be operational to run your business will assist you in determining which components require the highest level of security.
4. Track devices and users
Anyone with access to your network also has access to all your business contacts, resources, secrets, and other confidential data. You may want to assign this task to the most trustworthy persons in your team and keep track of their network-related activities. There’s no harm in being a little cautious.
The same goes for your hardware and software. Ensure your devices do not consume large portions of bandwidth and hamper your workflow.
5. Set up alerts
Tracking and monitoring are useless without setting up alerts that ring the alarm at the slightest discrepancy. Real-time alerts are critical to red-flagging problems before they become emergencies. Creating real-time alerts needs no rocket science. All you need is a robust dashboard to keep an eye on your network health indicators and maintain and clear view of the situation.
6. Automate whatever you can
Invest in a robust and reliable network management software to automate:
- Network performance monitoring
- Security patch implementation
- Data backup
Automation will give you a much-needed respite from human errors and time-consuming tasks. It will allow your staff to take up core business functions without extra work.
7. Train and update your staff
You cannot expect all your staff to be technically sound and well-informed about phishing scams and cyber threats. The onus is on you to train all your staff about identifying network vulnerabilities and the ways to solve them. Administrators can prevent costly disruptions by ensuring staff is up-to-date on all aspects of network management.
8. Test your network
Testing can simplify your network management and make it quick but effective. Hire reliable network security and management experts like our CMIT team from Roanoake to identify and resolve any issues before they go out of hand. Furthermore, testing also gives insights into areas that require immediate upgrades as per the latest technology.
9. Gather data for future planning
Your network should grow to accommodate your company’s requirements and expansions. To grow, you need to plan. Planning requires accurate, real-time, reliable, and in-depth insights, which you can only obtain from your network. By understanding how the network is being used, network managers can make informed decisions about capacity planning and avoid over or under-buying resources.
10. Prepare for potential network failures
Networking is a complex process that involves hundreds or even thousands of pieces of hardware, software, systems, and protocols. An outage in one of the core network components can shut down your entire business operations if it occurs.
By creating redundancy in components most likely to fail, you can mitigate the risk of network failures. Creating network redundancy begins with analyzing your current network architecture/infrastructure to identify risk areas. There are several common points of failure risk, including:
- Your Local Area Network
- Core site
- Routing
- Routing protocols
- Hardware
You can shore up your network by creating redundant sources like:
- Failover solutions
- Load balancers
- Redundant power supplies
- Off-site data backup
Takeaway
Network management is much work and trying to tick all the boxes can burden your staff. You can implement best practices of network security to build efficient network defenses and ward off potential security threats. CMIT Solutions offers perfectly orchestrated proactive management of all networks. Want to know how we can help you? Feel free to call us! Eliminate your future security threats with CMIT’s effective network management!
CMIT Solutions of Roanoke offers enterprise-grade IT support and cybersecurity solutions to businesses in Christiansburg, Blacksburg, Radford, and Wytheville. Partner with us for proactive management and peace of mind across the Commonwealth of Virginia.
Our IT Services
| Managed IT Services | Cybersecurity | Productivity Applications |
| IT Support | Cloud Services | Network Management |
| Compliance | Data Backup | Unified Communications |
| IT Guidance | IT Procurement |