Cybersecurity Services
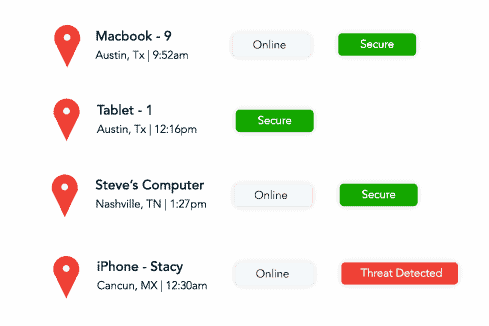
CMIT Solutions provides robust cybersecurity solutions tailored to protect businesses against evolving threats like ransomware, malware, and unauthorized access. Their services include:
- Firewall Protection: Acts as a barrier to prevent unauthorized access while ensuring secure data exchange.
- Access Control: Manages and restricts employee access to sensitive systems, ensuring data privacy.
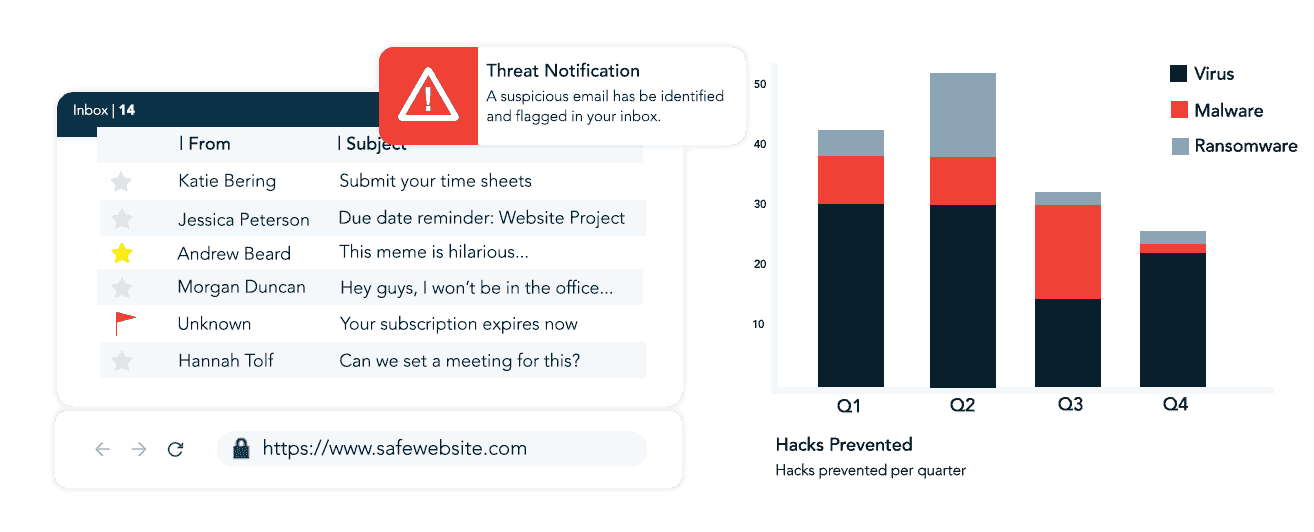
- Intrusion Prevention Systems (IPS): Detects and neutralizes potential intrusions in real time.
- Data Loss Prevention (DLP): Implements policies to prevent unauthorized data sharing.
- Cloud Security: Secures cloud-based data and applications against breaches.
These measures ensure a multi-layered defense system for small to medium-sized businesses, enabling safer operations.


 Managed Services
Managed Services
 Cybersecurity
Cybersecurity
 Productivity Applications
Productivity Applications
 IT Support
IT Support
 Cloud Services
Cloud Services
 Network Management
Network Management
 Compliance
Compliance
 Data Backup
Data Backup
 Unified Communications
Unified Communications
 IT Guidance
IT Guidance
 IT Procurement
IT Procurement