FAQs on Cyber Protection Solutions
Who Needs Cybersecurity Support?
Any company using digital technology to store or access sensitive data or financial records needs cybersecurity solutions. Organizations of any size are susceptible to cyber threats and must take proactive steps to safeguard against these attacks. These solutions should include implementing authentication procedures, utilizing cloud storage platforms, and investing in intrusion detection systems.
Multi-layered cybersecurity solutions provide the best protection against the devastating impact of cyberattacks. An effective cybersecurity strategy can include penetration testing, threat hunting, or cloud-based services that monitor systems and networks. Implementing best practices in information security, such as following proper encryption protocols, disabling unnecessary accounts, and providing secure software updates, is also essential for companies looking to stay safe from cyber threats.
Cyber threats constantly evolve, from viruses to spyware to small business ransomware, so companies should remain informed about the latest developments and advancements in cybersecurity. Businesses should invest in the proper equipment, training, and security measures to secure data. Utilizing best practices in security and investing in tailored solutions can go a long way in preventing data loss and reducing cyber risks, meeting insurance requirements, and complying with regulations.
What Does Cybersecurity Support Include?
CMIT Solutions provides comprehensive IT services and cybersecurity solutions to businesses of all sizes. We understand the potential risk of cyber threats, and the critical role that cybersecurity plays in any modern business. That’s why our cybersecurity support services include much more than just preventing cyberattacks.
We can assist with cybersecurity by providing a wide range of software products that help to protect confidential information from cyber activities and data theft. Our security solutions offer assistance in determining the extent of the risks and provide advice for mitigating threats, all while protecting company data under the necessary data compliance regulations.
We understand that every business faces different cybersecurity issues, so we offer tailored services to provide the highest level of security available. From advice on avoiding malicious software and implementing robust firewalls to user management, our experienced staff provides round-the-clock cybersecurity support to ensure your data remains safe.
For any business looking to secure its IT environment and comply with data protection regulations, CMIT Solutions has the solutions and services to get the job done. Our knowledgeable team and state-of-the-art tech give you peace of mind from cyber threats.
What Are the Most Important Components of a Cybersecurity Package?
The potential for cyber threats and attacks is growing as more companies and organizations are connected online. As a result, organizations need to consider the importance of having comprehensive cybersecurity solutions in place. At CMIT Solutions, we believe that understanding the components of a comprehensive cybersecurity package is essential for protecting a business’s data and keeping its customers safe.
In our opinion, the most crucial components of a comprehensive cybersecurity package include the following:
Data Compliance
Data compliance involves confirming that the organization complies with all relevant laws and regulations. This can include installing antivirus software and maintaining backups of all data.
Software Products
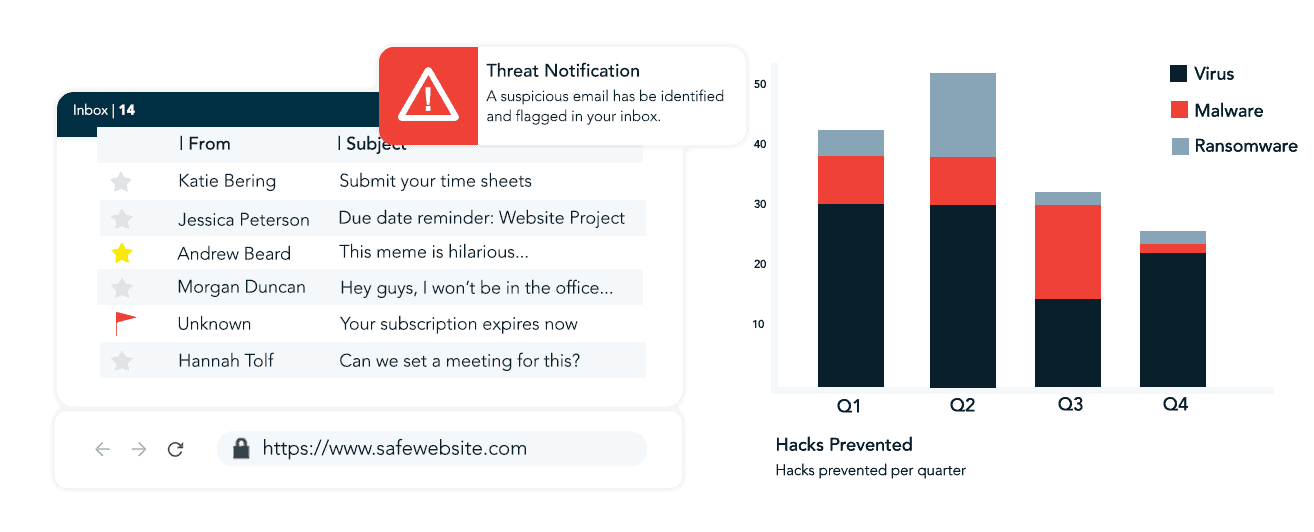
Implementing tailored software helps defend against potential risks. This could involve software that blocks access to sites, tracks activity on the network, or blocks suspicious email messages.
Cyber Threat Awareness
Employees and customers must be aware of potential threats and ways to avoid or minimize their risks. This may include informing employees about phishing attempts, providing ongoing security training, and enforcing strong password policies.
Mitigate Potential Risk
It’s essential to develop plans to address any potential risk that may occur in the event of a cyberattack. This may involve incident-response planning, data loss prevention policies, and penetration testing.
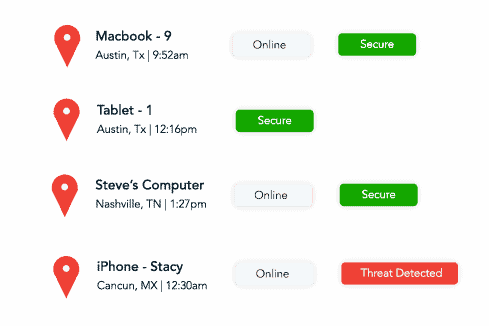
Monitor Cyber Activities
Cybersecurity monitoring through Security Operations Center (SOC) or Security Incident and Event Monitoring (SIEM) services is an important part of an effective defense strategy. Creating processes and procedures and implementing cybersecurity solutions to monitor and log all activities on the organization’s networks, systems and databases can help to identify any malicious or suspicious activity and prevent potential cyber threats.